The $4 Million Wake-Up Call
Last year, I watched a mid-sized tech company nearly collapse overnight. Their story started like many others – a disgruntled IT admin with excessive privileges decided to take revenge before leaving. Within hours, critical systems were compromised, customer data was at risk, and the company faced a potential $4 million lawsuit. The culprit? Poor managing privileged access practices that gave one person too much power.
If this scenario sends chills down your spine, you’re not alone. Privileged access mismanagement remains one of the top cybersecurity threats facing organizations today. This guide will walk you through proven strategies to secure your privileged accounts, implement robust PAM best practices, and protect your organization from both external threats and insider risks.
What Exactly is Privileged Access Management?
Think of privileged access like the master keys to your digital kingdom. Just as you wouldn’t hand out master keys to every employee in a physical building, privileged access management (PAM) controls who gets the digital “keys” to your most sensitive systems and data.
PAM encompasses the policies, technologies, and procedures used to secure, control, and monitor access to privileged accounts – those special accounts with elevated permissions that can make significant changes to your IT infrastructure.
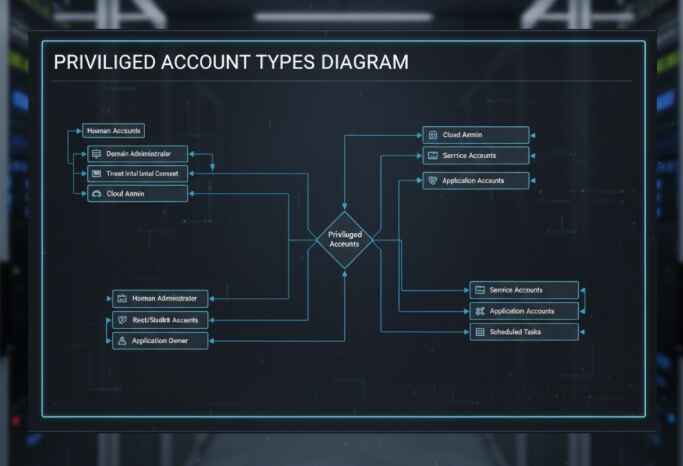
Common Types of Privileged Accounts
Understanding what you’re protecting is the first step. Here are the most common privileged account types lurking in your network:
- Administrative accounts (domain admins, local admins)
- Service accounts (applications, databases, network services)
- Emergency access accounts (break-glass accounts)
- Shared accounts (generic admin accounts)
- Application accounts (ERP, CRM system administrators)
The Foundation: Implementing Least Privilege Principle
The least privilege principle is like giving someone exactly the right size key for the door they need to open – nothing more, nothing less. This fundamental concept ensures users receive the minimum access rights necessary to perform their job functions.
Here’s how to implement it effectively:
1. Conduct a Comprehensive Access Audit
Start by mapping every privileged account in your organization. I’ve seen companies discover hundreds of forgotten admin accounts during their first audit. Use automated discovery tools to identify:
- Active privileged accounts
- Dormant accounts that should be disabled
- Shared accounts that need individual alternatives
- Over-privileged regular user accounts
2. Implement Role-Based Access Control (RBAC)
Create specific roles with predefined permission sets instead of granting blanket administrative access. For example:
- Database Admin: Access to database management tools only
- Network Admin: Network equipment configuration rights
- Security Admin: Security tool and policy management access
Just-in-Time Access: Your New Best Friend
Just-in-time privileged access is like having a smart lock that only opens when needed and automatically locks again. This approach grants temporary elevated privileges for specific tasks and automatically revokes them afterward.
Benefits include:
- Reduced attack surface (fewer standing privileges)
- Better audit trails
- Elimination of “privilege creep”
- Compliance with regulatory requirements
Multi-Factor Authentication: The Non-Negotiable Layer
If passwords are the front door lock, multi-factor authentication PAM is the security system, guard dog, and reinforced door frame all rolled into one. Never – and I mean never – allow privileged account access with just a username and password.
Modern MFA options for privileged access include:
- Hardware tokens
- Mobile push notifications
- Biometric authentication
- Certificate-based authentication
Password Vaulting and Automated Rotation
Password vaulting centralizes storage of privileged credentials in encrypted repositories. Think of it as a high-security bank vault for your passwords, but with some serious automation capabilities.
Key features to look for:
- Automated password rotation: Changes passwords on a schedule
- Check-in/check-out functionality: Tracks who accessed what and when
- Session recording: Records privileged sessions for compliance
- Emergency access procedures: Break-glass access when systems are down
| Feature | Benefit | Implementation Priority |
|---|---|---|
| Password Vaulting | Centralized credential security | High |
| Automated Rotation | Reduces credential theft risk | High |
| Session Recording | Compliance and forensics | Medium |
| Emergency Access | Business continuity | High |
Monitoring and Session Management
Privileged user monitoring is your organization’s security camera system for digital activities. You need to know not just who accessed what, but exactly what they did once they got there.
Essential monitoring capabilities:
- Real-time session monitoring
- Keystroke logging and screen recording
- Behavioral analytics and anomaly detection
- Automated alerts for suspicious activities
- Comprehensive audit trails
Zero Trust Architecture Integration
The Zero Trust privileged access model operates on a simple principle: “Never trust, always verify.” This approach assumes that threats exist both inside and outside your network perimeter.
Core Zero Trust PAM components:
- Continuous authentication and authorization
- Micro-segmentation of privileged access
- Risk-based access decisions
- Comprehensive logging and monitoring
Third-Party and Vendor Access Management
Managing third-party privileged access requires special attention. External vendors often need temporary access to your systems, creating unique security challenges.
Best practices include:
- Time-limited access provisioning
- Dedicated vendor accounts (no shared credentials)
- Enhanced monitoring and session recording
- Clear access termination procedures
- Regular access reviews and certifications
Top PAM Solutions to Consider
Based on current market analysis and user feedback, here are leading PAM solutions worth evaluating:
Enterprise-Grade Options:
- CyberArk Privileged Access Security: Comprehensive platform with advanced threat analytics
- BeyondTrust Privileged Access Management: Strong just-in-time access capabilities
- Thycotic Secret Server: Excellent password rotation and compliance features
Mid-Market Solutions:
- ManageEngine PAM360: Good integration with business workflows
- One Identity Safeguard: Focus on automation and session monitoring
- Wallix Bastion: Simplified deployment with strong compliance features
Cloud-Native Options:
- Microsoft Azure AD Privileged Identity Management: Integrated with Microsoft ecosystem
- HashiCorp Vault: Developer-friendly secrets management
- Centrify Privileged Access Service: Cloud-ready with strong MFA integration
Implementation Roadmap
Rolling out PAM isn’t a weekend project. Here’s a practical implementation approach:
Phase 1: Discovery and Planning (Weeks 1-4)
- Inventory all privileged accounts
- Assess current security gaps
- Define PAM requirements and goals
- Select appropriate PAM solution
Phase 2: Core Implementation (Weeks 5-12)
- Deploy password vaulting
- Implement basic access controls
- Set up MFA for privileged accounts
- Begin automated password rotation
Phase 3: Advanced Features (Weeks 13-20)
- Enable session monitoring and recording
- Implement just-in-time access
- Deploy behavioral analytics
- Integrate with existing security tools
Phase 4: Optimization (Ongoing)
- Regular access reviews and certifications
- Policy refinements based on usage patterns
- Security awareness training
- Continuous monitoring and improvement
Compliance and Regulatory Considerations
Modern PAM tools for compliance help organizations meet various regulatory requirements:
- SOX: Financial controls and audit trails
- PCI-DSS: Payment card data protection
- HIPAA: Healthcare data security
- GDPR: EU data protection regulations
- ISO 27001: Information security management
Common Implementation Pitfalls to Avoid
Learning from others’ mistakes can save you time, money, and headaches:
- Over-complicating initial deployment: Start simple, then add complexity
- Inadequate user training: Even the best tools fail with poor adoption
- Ignoring business workflows: PAM should enhance, not hinder productivity
- Insufficient testing: Always test in non-production environments first
- Neglecting ongoing maintenance: PAM requires continuous attention and updates
Measuring PAM Success
Track these key metrics to gauge your PAM program effectiveness:
- Privileged account inventory accuracy (aim for 100%)
- Password rotation compliance (target 95%+)
- Session monitoring coverage (monitor all privileged sessions)
- Time to access provisioning (minimize while maintaining security)
- Security incident reduction (measure year-over-year improvement)
The Road Ahead: Future of Privileged Access
The PAM landscape continues evolving with emerging technologies:
- AI-powered behavioral analytics for anomaly detection
- Quantum-resistant encryption for future-proofing
- Cloud-native PAM architectures for modern infrastructures
- Integration with DevSecOps pipelines for automated security
Conclusion
Managing privileged access isn’t just about buying the right tools – it’s about implementing a comprehensive strategy that balances security with operational efficiency. The companies that succeed are those that treat PAM as an ongoing journey rather than a one-time project.
Remember that disgruntled IT admin I mentioned? His former company now has robust PAM controls in place, including session monitoring, just-in-time access, and automated credential rotation. They’ve transformed from a security liability into a trusted partner for their clients.
Take action today: Start with a privileged account audit, implement MFA on all administrative accounts, and begin planning your comprehensive PAM strategy. Your future self (and your organization’s security posture) will thank you.
What’s your biggest privileged access management challenge? Share your experiences in the comments below, or reach out to discuss how these strategies might work in your specific environment.
Frequently Asked Questions
How often should privileged accounts be audited?
Privileged accounts should be audited quarterly at minimum, with high-risk accounts reviewed monthly. Many organizations implement continuous monitoring alongside formal quarterly reviews. Critical accounts like domain administrators may require weekly or even daily verification of access appropriateness.
What’s the difference between PAM and regular Identity Access Management (IAM)?
PAM focuses specifically on high-risk, high-privilege accounts with elevated permissions, while IAM manages standard user identities and access rights. PAM typically includes specialized features like session recording, password vaulting, and just-in-time access that aren’t necessary for regular user accounts. Think of PAM as a specialized subset of IAM for your most sensitive access requirements.
How can automation improve privileged access lifecycle management?
Automated privileged access management streamlines the entire lifecycle from provisioning to deprovisioning. Key automation capabilities include scheduled password rotations, automatic account discovery, policy-based access approvals, and triggered access reviews. This reduces manual errors, ensures consistency, and provides better audit trails while freeing up IT teams for strategic work.
What compliance standards require privileged access controls?
Most major compliance frameworks mandate privileged access controls, including SOX (financial reporting), PCI-DSS (payment data), HIPAA (healthcare), GDPR (data protection), and ISO 27001 (information security). Each has specific requirements for access monitoring, credential management, and audit trails that modern PAM solutions can help address.
How does Zero Trust architecture support privileged access management?
Zero Trust privileged access eliminates the traditional network perimeter model by requiring continuous verification for every access request. This means privileged users must authenticate and authorize each session, regardless of their location or previous access history. Zero Trust PAM includes micro-segmentation, behavioral analytics, and risk-based access decisions to minimize breach impact.
What are the main risks of shared privileged accounts?
Shared privileged accounts create accountability gaps (you can’t track individual actions), increase credential exposure risks, complicate access management, and hinder compliance efforts. Best practices include eliminating shared accounts where possible, implementing named accounts with appropriate permissions, and using PAM tools to manage any remaining shared credentials with proper check-out procedures and session monitoring.
Sources: