Introduction
Three months ago, my colleague Sarah watched in horror as hackers moved laterally through their company’s network like they owned the place. What started as a simple phishing email turned into a full-scale data breach because once inside the perimeter, the attackers had free rein. That incident became our wake-up call to start implementing Zero Trust Security Models—and honestly, it’s been a game-changer.
Zero Trust isn’t just another security buzzword; it’s a fundamental shift from “trust but verify” to “never trust, always verify.” If you’re tired of playing cybersecurity defense with outdated castle-and-moat strategies, this comprehensive guide will show you exactly how to implement Zero Trust in your organization.
You’ll discover the core principles, learn about essential technologies, and get practical steps to build a robust Zero Trust architecture that actually protects against modern threats.
What Is Zero Trust Security and Why It Matters Now
Zero Trust Security Models operate on a simple but powerful principle: trust nothing, verify everything. Unlike traditional security that assumes internal network traffic is safe, Zero Trust treats every user, device, and connection as potentially hostile—even when they’re already inside your network.
The statistics are sobering. According to IBM’s Cost of a Data Breach Report, the average breach takes 287 days to identify and contain. With Zero Trust, that lateral movement Sarah’s company experienced becomes nearly impossible because every access request gets scrutinized in real-time.
Think of it like airport security. Traditional network security was like having guards at the airport entrance but letting everyone roam freely once inside. Zero Trust is like having checkpoints at every gate, every bathroom, and every coffee shop—annoying? Maybe. Effective? Absolutely.
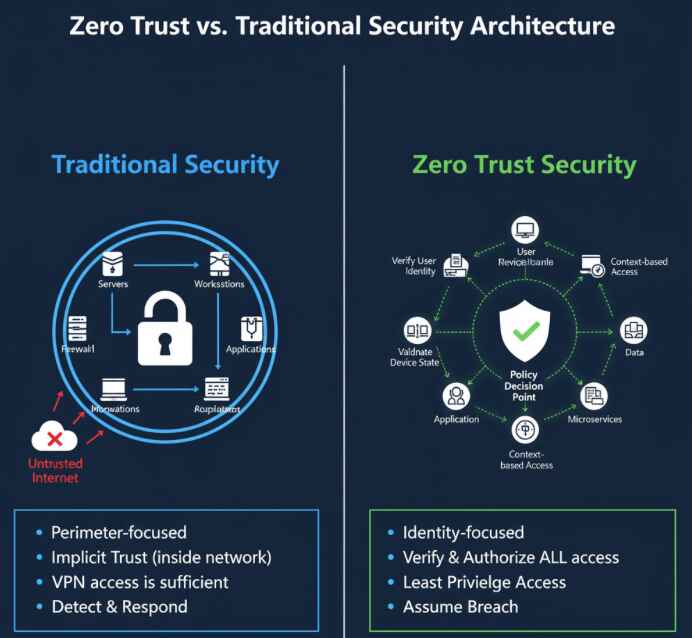
Core Principles of Zero Trust Architecture
1. Verify Every User and Device
Identity and Access Management (IAM) forms the backbone of any Zero Trust implementation. Every access request triggers authentication, regardless of location or previous access history.
Key components include:
- Multi-Factor Authentication (MFA): Beyond passwords
- Continuous identity verification
- Risk-based authentication
- Device health validation
2. Enforce Least Privilege Access
Grant users the minimum access needed for their job—nothing more. This principle dramatically reduces attack surfaces and limits potential damage from compromised accounts.
3. Assume Breach and Verify Explicitly
Never trust, always verify. Every transaction gets evaluated based on multiple signals: user identity, device health, location, and behavioral patterns.
Essential Technologies for Zero Trust Implementation
Zero Trust Network Access (ZTNA)
ZTNA replaces traditional VPNs with application-specific access controls. Instead of giving broad network access, users connect directly to specific applications they need.
Benefits of ZTNA:
- Granular access control
- Reduced attack surface
- Better user experience
- Cloud-native scalability
Microsegmentation: Building Digital Walls
Microsegmentation creates secure zones within your network, preventing lateral movement. It’s like having fireproof compartments in a building—if one area gets compromised, the fire doesn’t spread.
Advanced microsegmentation involves:
- Application-layer enforcement
- Real-time policy adjustment
- Workload protection
- East-west traffic monitoring
Continuous Monitoring and Analytics
Zero Trust requires continuous monitoring to detect anomalies and adjust policies in real-time. Machine learning algorithms analyze user behavior patterns to spot potential threats.
Step-by-Step Zero Trust Implementation Guide
Phase 1: Assessment and Planning (Months 1-2)
Start with a comprehensive audit of your current security posture:
- Inventory all assets: Users, devices, applications, data
- Map data flows: Understand how information moves through your organization
- Identify critical resources: What needs the highest protection?
- Assess current security gaps: Where are you vulnerable?
Phase 2: Foundation Building (Months 3-6)
Focus on establishing core Zero Trust capabilities:
Identity and Access Management:
- Deploy MFA across all systems
- Implement single sign-on (SSO)
- Establish identity governance processes
Device Management:
- Implement endpoint detection and response (EDR)
- Deploy device compliance policies
- Establish device trust scoring
Phase 3: Network Transformation (Months 6-12)
Replace traditional network access with Zero Trust alternatives:
- Deploy ZTNA solutions
- Implement microsegmentation
- Replace VPNs with secure access service edge (SASE)
- Establish network policy enforcement
Overcoming Common Zero Trust Implementation Challenges
User Resistance and Training
Change is hard, especially when it involves additional security steps. We learned this the hard way when our initial rollout faced significant pushback.
Solution strategies:
- Gradual rollout with pilot groups
- Comprehensive user training
- Clear communication about benefits
- Streamlined user experience
Legacy System Integration
Not every application supports modern authentication protocols. You’ll need creative solutions for older systems.
Workaround approaches:
- Identity bridges and proxies
- Privileged access management (PAM)
- Network-based controls for legacy apps
- Planned modernization roadmaps
Budget and Resource Constraints
Zero Trust implementation isn’t cheap, but the cost of doing nothing is higher.
| Implementation Phase | Typical Cost Range | Key Investments |
|---|---|---|
| Assessment & Planning | $50K – $200K | Consulting, tools, training |
| Foundation Building | $200K – $800K | IAM platforms, MFA, EDR |
| Network Transformation | $500K – $2M | ZTNA, microsegmentation, SASE |
Top Zero Trust Solutions for 2025
Based on current market analysis, here are standout solutions for different organizational needs:
For Enterprise Organizations:
- Microsoft Azure Entra ID: Comprehensive identity platform with advanced conditional access
- Okta Identity Cloud: Market-leading IAM with extensive integrations
- Cisco AnyConnect & Duo Security: Full-stack security with seamless integration
For Mid-Market Companies:
- Zscaler Zero Trust Exchange: Cloud-delivered platform without VPN complexity
- Palo Alto Networks Prisma Access: Comprehensive SASE solution
- CrowdStrike Falcon Zero Trust: Endpoint-centric approach with behavioral analytics
For Growing Businesses:
- Twingate: Simple, easy-to-deploy ZTNA solution
- NordLayer: Cloud-native platform with competitive pricing
- JumpCloud Open Directory: Unified directory with Zero Trust capabilities
Measuring Zero Trust Success
You can’t improve what you don’t measure. Key metrics for Zero Trust effectiveness include:
Security Metrics:
- Mean time to detection (MTTD)
- Lateral movement incidents
- Privileged access violations
- Policy compliance rates
Business Metrics:
- User productivity scores
- IT support ticket volume
- Compliance audit results
- Business continuity metrics
The Future of Zero Trust Security
Zero Trust continues evolving with emerging technologies. AI-driven security is becoming more sophisticated, while quantum-resistant encryption prepares us for future threats. Cloud-native architectures are making Zero Trust more accessible to organizations of all sizes.
The trend toward hybrid workforces makes Zero Trust not just beneficial but essential. As the boundaries between office and remote work blur, traditional perimeter security becomes meaningless.
Conclusion
Implementing Zero Trust Security Models isn’t just about technology—it’s about fundamentally changing how your organization thinks about security. The journey requires commitment, resources, and patience, but the payoff in reduced risk and improved security posture is substantial.
Start with small wins: implement MFA, assess your current architecture, and begin planning your roadmap. Remember, Zero Trust is a journey, not a destination. Every step forward makes your organization more secure and resilient.
Ready to begin your Zero Trust journey? Start by conducting a security assessment and identifying your most critical assets. Share this guide with your security team and let’s discuss your biggest implementation challenges in the comments below.
Frequently Asked Questions
How long does it typically take to fully implement Zero Trust Security Models?
A complete Zero Trust implementation typically takes 12-24 months, depending on organizational size and complexity. Most companies see initial benefits within 3-6 months by focusing on high-impact areas like identity management and MFA. The key is taking a phased approach rather than trying to transform everything at once.
Can Zero Trust work effectively for small and medium-sized businesses?
Absolutely! Cloud-based Zero Trust solutions have made implementation much more accessible for SMBs. Platforms like Twingate, NordLayer, and JumpCloud offer affordable, easy-to-deploy options that don’t require large IT teams. Many SMBs actually have advantages in implementation because they have less legacy infrastructure to work around.
What’s the difference between Zero Trust Network Access (ZTNA) and traditional VPNs?
While VPNs provide broad network access once authenticated, ZTNA grants access only to specific applications and resources. ZTNA also continuously verifies user identity and device health throughout the session, whereas VPNs typically authenticate once at connection. This makes ZTNA more secure and better suited for modern cloud environments.
How does Zero Trust impact user experience and productivity?
Initially, users may experience additional authentication steps, but modern Zero Trust solutions use risk-based authentication and single sign-on to minimize friction. Many organizations report improved productivity long-term because users can securely access resources from anywhere without complex VPN connections or IT support tickets.
What role does artificial intelligence play in Zero Trust implementation?
AI enhances Zero Trust through behavioral analytics, anomaly detection, and automated policy enforcement. Machine learning algorithms analyze user patterns to identify suspicious activities and adjust security policies in real-time. This allows for more sophisticated threat detection while reducing false positives that could impact user experience.
Sources: