Last Tuesday, I got a panicked call from a client whose small marketing agency had been locked out of their entire system. “We can’t access anything,” Sarah whispered, as if speaking louder might make it worse. “There’s a message saying we need to pay $50,000 in Bitcoin.”
This wasn’t just another cautionary tale—it was a harsh reminder that Essential Information Security Practices for Businesses aren’t optional anymore. They’re the difference between thriving and closing your doors.
Whether you’re running a five-person startup or managing a 500-employee corporation, cyber threats don’t discriminate. In this guide, we’ll walk through the fundamental security practices that can protect your business, your customers, and your reputation. No technical jargon, no overwhelming complexity—just practical steps that actually work.
Why Business Cybersecurity Can’t Wait Until Tomorrow
Here’s the uncomfortable truth: cybercriminals are getting smarter while many businesses are falling further behind. The average cost of a data breach in 2025 exceeds $4.5 million, but for small businesses, even a “minor” incident can be devastating.
I’ve witnessed companies recover from natural disasters faster than they bounce back from cyber attacks. The difference? You can rebuild physical infrastructure, but rebuilding customer trust? That’s much harder.
The stakes have never been higher because:
- Remote work expanded attack surfaces dramatically
- Ransomware groups now target smaller businesses specifically
- Regulatory compliance requirements are tightening globally
- Customer expectations for data protection continue rising
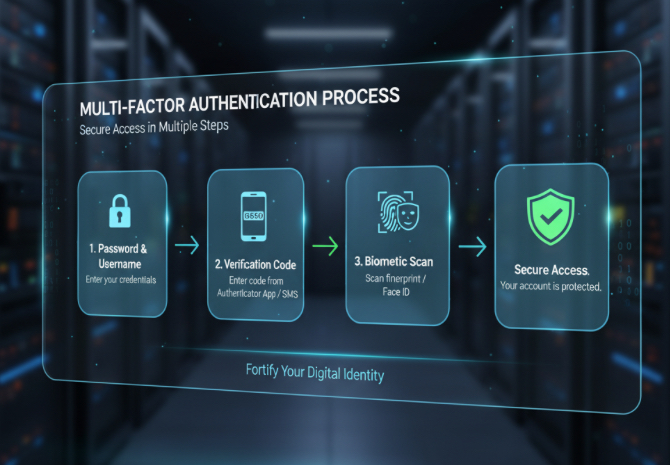
Foundation Layer: Multi-Factor Authentication and Access Controls
Let’s start with the basics that make the biggest difference. Multi-factor authentication (MFA) isn’t just another IT buzzword—it’s your first line of defense against 99.9% of automated attacks.
Think of MFA like a bank vault. Even if someone steals your key (password), they still can’t get inside without the combination (second factor) and biometric scan (third factor). Simple concept, massive protection boost.
Implementing MFA Across Your Organization
Start with these critical systems:
- Email accounts (especially admin accounts)
- Cloud storage and collaboration platforms
- Financial and accounting software
- Customer relationship management (CRM) systems
- Any system containing sensitive customer data
The beauty of modern MFA solutions is their simplicity. Employees can authenticate using smartphone apps, hardware tokens, or even biometric scanners. No more excuses about complexity or user friction.
Data Protection Best Practices: Beyond Basic Backups
Data encryption should be non-negotiable, but here’s what most guides don’t tell you: encryption is worthless if you’re not doing it correctly.
I learned this lesson while consulting for a healthcare practice that thought their “encrypted” patient records were secure. Turns out, they were using outdated encryption standards that modern tools could crack in hours, not years.
The Three-Layer Encryption Strategy
Layer 1: Data at Rest
- Encrypt all stored data using AES-256 standards
- Secure database encryption with proper key management
- Full-disk encryption for all business devices
Layer 2: Data in Transit
- HTTPS for all web communications
- Encrypted email for sensitive communications
- VPN for remote access connections
Layer 3: Data in Use
- Application-level encryption for active data processing
- Secure memory handling in custom applications
- Regular encryption key rotation schedules
Network Security: Building Digital Fortress Walls
Your network security strategy should follow the “Swiss cheese model”—multiple layers with different holes, so no single point of failure can compromise everything.
Modern businesses need more than traditional firewalls. You need intelligent threat detection, network segmentation, and real-time monitoring. But don’t worry—you don’t need a computer science degree to implement these effectively.
Essential Network Protection Components
| Security Layer | Purpose | Best Practices |
|---|---|---|
| Perimeter Firewall | Block unauthorized access | Configure deny-by-default rules, regular updates |
| Network Segmentation | Isolate critical systems | Separate guest, employee, and server networks |
| Intrusion Detection | Monitor for suspicious activity | Real-time alerts, automated response capabilities |
| DNS Filtering | Block malicious websites | Cloud-based filtering, regular blacklist updates |
Employee Training: Your Human Firewall
Here’s something that might surprise you: employee cybersecurity awareness training is more effective than most expensive security software. Why? Because humans are involved in 95% of successful cyber attacks.
But forget boring PowerPoint presentations about password complexity. Modern security training needs to be engaging, relevant, and regularly updated.
Building a Security-Conscious Culture
Monthly micro-training sessions work better than annual marathon workshops. Focus on:
- Real phishing examples targeting your industry
- Hands-on exercises with company-specific scenarios
- Regular simulated phishing tests (with rewards, not punishment)
- Clear reporting procedures for suspicious activities
The goal isn’t to make employees paranoid—it’s to make security awareness automatic, like checking both ways before crossing the street.
Incident Response Planning: When Prevention Isn’t Enough
Even with perfect security practices, incidents can happen. The difference between a minor disruption and a business-ending catastrophe often comes down to how quickly and effectively you respond.
Your incident response plan should answer these questions:
- Who needs to be notified first?
- What systems should be isolated immediately?
- How will you communicate with customers and stakeholders?
- What evidence needs to be preserved for investigation?
- When should law enforcement be contacted?
I’ve seen companies recover from major breaches in days because they had practiced their response plan. I’ve also watched organizations struggle for months because they were figuring things out as they went.
Essential Security Tools: Building Your Defense Stack
The right security tools can automate much of your protection, but choosing the wrong ones wastes money and creates false confidence. Here’s what actually matters:
Core Security Stack:
- Endpoint Protection: Solutions like CrowdStrike Falcon or Microsoft Defender for Business
- Email Security: Proofpoint Email Protection or similar anti-phishing tools
- Backup Solutions: Automated, tested backups with offline copies (Acronis Cyber Protect)
- Identity Management: Okta Identity Cloud or Duo Security for MFA
- Network Monitoring: Real-time threat detection and response capabilities
Cloud Migration and Cybersecurity: New Opportunities, New Risks
Cloud migration creates incredible opportunities but also introduces new security considerations. The biggest mistake? Assuming your cloud provider handles all security responsibilities.
Cloud security operates on a “shared responsibility model.” Your provider secures the infrastructure; you secure everything you put on it. Miss this distinction, and you’re setting yourself up for problems.
Cloud security essentials:
- Proper identity and access management (IAM) configuration
- Regular security audits of cloud permissions
- Data loss prevention (DLP) policies
- Multi-region backup strategies
- Clear data governance policies
Measuring Security Success: KPIs That Matter
How do you know if your cyber threat prevention efforts are working? Track these meaningful metrics:
- Time to detect security incidents (target: under 24 hours)
- Employee security training completion rates (target: 100% quarterly)
- Successful phishing simulation click rates (target: under 5%)
- System uptime during security updates (target: 99.5%+)
- Third-party security assessment scores (annual penetration testing)
Looking Ahead: Preparing for Future Threats
Cybersecurity isn’t a destination—it’s an ongoing journey. As artificial intelligence makes attacks more sophisticated, businesses need to evolve their defensive strategies continuously.
Emerging trends to watch:
- AI-powered threat detection and response
- Zero-trust security architecture
- Quantum-resistant encryption standards
- Automated compliance monitoring
- Enhanced privacy regulations globally
Conclusion: Your Security Journey Starts Now
Implementing Essential Information Security Practices for Businesses doesn’t have to be overwhelming. Start with the fundamentals: strong authentication, regular backups, employee training, and incident response planning. Build from there as your comfort and capabilities grow.
Remember Sarah’s marketing agency from the introduction? They recovered because they had implemented basic security practices six months earlier. Their backups were current, their incident response plan was clear, and their team knew what to do. What could have been a business-ending disaster became a temporary inconvenience.
Your business deserves the same protection. Start today, improve continuously, and stay vigilant. The investment you make in cybersecurity today could save your business tomorrow.
Ready to strengthen your security posture? Download our free security assessment checklist, or share this guide with other business owners who need to prioritize their digital protection. Have questions about implementing these practices? Drop them in the comments below—I read and respond to every one.
Frequently Asked Questions
What are the most critical information security practices every business should implement first?
Start with these four foundational practices: enable multi-factor authentication on all business accounts, implement automated data backups with offline copies, establish basic employee security training, and deploy endpoint protection software. These four practices alone can prevent 80% of common cyber attacks while being relatively simple and cost-effective to implement.
How often should businesses update their cybersecurity policies and procedures?
Review and update cybersecurity policies quarterly, with major revisions annually. However, trigger immediate updates when experiencing security incidents, implementing new technology, or when regulations change. The threat landscape evolves rapidly, so your policies must keep pace. Many successful businesses conduct monthly “policy spot checks” to ensure procedures remain current and effective.
What’s the difference between basic antivirus and comprehensive endpoint protection?
Traditional antivirus software relies on signature-based detection to identify known malware, while comprehensive endpoint protection platforms use behavioral analysis, machine learning, and real-time threat intelligence to detect both known and unknown threats. Modern solutions like CrowdStrike Falcon or Sophos Intercept X can stop zero-day attacks and provide incident response capabilities that basic antivirus cannot match.
How can small businesses protect themselves from ransomware without breaking the budget?
Implement the “3-2-1 backup rule” (3 copies of data, 2 different media types, 1 offsite), enable automatic software updates, train employees to recognize phishing emails, and use cloud-based security solutions that provide enterprise-grade protection at small business prices. Solutions like Microsoft Defender for Business or Bitdefender GravityZone offer comprehensive ransomware protection starting under $3 per user monthly.
What should businesses do immediately after discovering a potential security breach?
Follow these immediate steps: isolate affected systems to prevent spread, notify your incident response team, preserve evidence for investigation, assess the scope of compromise, notify relevant stakeholders according to your communication plan, and document all response activities. Don’t attempt to “fix” things immediately—proper containment and assessment prevent turning a small incident into a major disaster.
How important is employee security training compared to technical security tools?
Employee training is crucial because humans are involved in 95% of successful cyber attacks. However, training and technology work together—neither alone is sufficient. Effective programs combine monthly micro-training sessions, simulated phishing tests, and clear reporting procedures with robust technical controls. Organizations with comprehensive training programs experience 70% fewer successful phishing attacks than those relying solely on technical solutions.
Sources: