Introduction
Picture this: You’re sipping your morning coffee at a local café, checking your bank account on their free Wi-Fi, when suddenly you wonder—could someone be watching? Last month, my neighbor discovered that their “secure” home network had been compromised for weeks, with hackers potentially accessing everything from family photos to financial documents. This wake-up call got me diving deep into data encryption techniques, and honestly, I wish I’d started learning about this years ago.
Data encryption isn’t just for tech experts or government agencies anymore. In our hyperconnected world, understanding basic encryption has become as essential as knowing how to lock your front door. Whether you’re a small business owner, a student, or someone who simply values privacy, this beginner’s guide to data encryption techniques will demystify the complex world of cryptography and show you practical ways to protect your digital life.
By the end of this article, you’ll understand the fundamental types of encryption, know which algorithms to trust, and have actionable steps to implement encryption in your daily digital routine.
What Is Data Encryption and Why Should You Care?
Data encryption transforms your readable information (called plaintext) into scrambled, unreadable code (called ciphertext) using mathematical algorithms. Think of it as creating a secret language that only authorized parties can understand—except this secret language is virtually unbreakable when implemented correctly.
The importance of encryption has skyrocketed in recent years. According to cybersecurity reports, data breaches affected over 422 million individuals in 2022 alone. However, properly encrypted data remains useless to cybercriminals, even if they manage to steal it.
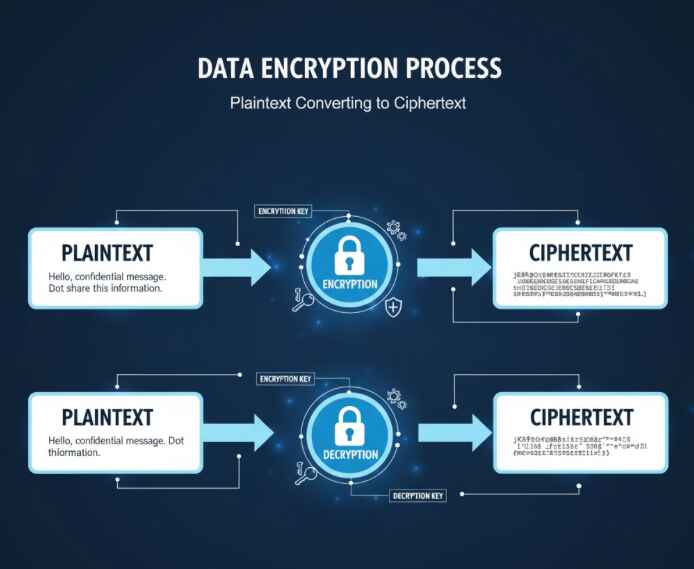
The Two Pillars of Encryption: Symmetric vs Asymmetric
Symmetric Encryption: The Shared Secret Method
Symmetric encryption uses the same key for both encrypting and decrypting data. Imagine you and your best friend agreeing on a secret code word—you both use the same “key” to encode and decode messages.
How symmetric encryption works:
- One key encrypts the data
- The same key decrypts the data
- Faster processing speeds
- Great for securing large amounts of data
Popular symmetric encryption algorithms:
- AES (Advanced Encryption Standard): The gold standard, used by governments worldwide
- DES (Data Encryption Standard): Older but still found in legacy systems
- 3DES: An enhanced version of DES
Asymmetric Encryption: The Public-Private Key Dance
Asymmetric encryption (also called public key cryptography) uses two different but mathematically related keys. It’s like having a special mailbox where anyone can deposit mail using a public key, but only you can retrieve it using your private key.
Key characteristics:
- Public key: Shared openly, used for encryption
- Private key: Kept secret, used for decryption
- Slower than symmetric encryption
- Perfect for secure communications between strangers
Leading asymmetric encryption algorithms:
- RSA encryption: Named after Rivest, Shamir, and Adleman
- Elliptic Curve Cryptography (ECC): More efficient than RSA
- Diffie-Hellman: Primarily for key exchange
Understanding Advanced Encryption Standard (AES)
AES has become the backbone of modern data security encryption. Adopted by the U.S. government in 2001, it’s now the most widely used symmetric encryption algorithm globally.
AES comes in three key lengths:
- AES-128: Good for most personal use
- AES-192: Enhanced security
- AES-256: Military-grade protection
What makes AES special? It’s been tested by cryptographers worldwide for over two decades and remains unbroken. Major tech companies like Google, Apple, and Microsoft rely on AES to protect billions of users’ data.
Hashing: The One-Way Street of Encryption
While not technically encryption, hashing encryption deserves mention in any encryption guide. Hash functions create unique digital fingerprints of data that cannot be reversed.
Common uses for hashing:
- Password storage
- Digital signatures
- Data integrity verification
- Blockchain technology
Popular hash algorithms include SHA-256, MD5 (now considered weak), and SHA-3.
Protecting Data at Rest vs Data in Transit
Encryption for Data at Rest
This protects stored information on your devices, servers, or cloud storage. Think of it as putting your valuables in a digital safe.
Best practices:
- Use full disk encryption (like BitLocker or FileVault)
- Encrypt sensitive files individually
- Secure database encryption for businesses
Encryption for Data in Transit
This protects information traveling across networks, from your device to websites or email servers.
Key implementations:
- HTTPS for web browsing
- SSL/TLS for secure connections
- VPNs for network-level protection
- End-to-end encryption for messaging apps
Encryption Key Management: The Weak Link
Even the strongest encryption algorithm becomes useless with poor encryption key management. Keys are like the combination to your vault—lose them or let them fall into wrong hands, and your security crumbles.
Essential key management practices:
- Regular key rotation
- Secure key storage
- Access control and monitoring
- Backup and recovery procedures
| Encryption Type | Key Management | Speed | Best Use Case |
|---|---|---|---|
| Symmetric (AES) | Shared secret | Fast | Large data volumes |
| Asymmetric (RSA) | Public/Private pair | Slower | Secure communications |
| Hashing | No keys needed | Very fast | Data integrity |
Practical Encryption Tools for Beginners
Ready to start implementing encryption? Here are some beginner-friendly tools:
For Personal Use:
- VeraCrypt: Free, open-source disk encryption
- 7-Zip: File compression with AES-256 encryption
- Signal: End-to-end encrypted messaging
- ProtonMail: Encrypted email service
For Small Businesses:
- AxCrypt: Simple file encryption
- Boxcryptor: Cloud storage encryption
- BitLocker: Built into Windows Pro
Remember, the best encryption tool is one you’ll actually use consistently.
Common Encryption Myths Debunked
Myth 1: “Encryption slows down my computer significantly” Reality: Modern processors handle AES encryption with minimal performance impact.
Myth 2: “Only criminals need encryption” Reality: Everyone deserves privacy. Encryption protects journalists, activists, businesses, and regular citizens.
Myth 3: “Government backdoors make encryption safer” Reality: Any backdoor weakens security for everyone, including the good guys.
The Future of Data Encryption
Encryption continues evolving to meet new challenges. Quantum computing poses theoretical threats to current algorithms, leading to development of quantum-resistant encryption. Meanwhile, homomorphic encryption allows computations on encrypted data without decrypting it first—a game-changer for cloud computing privacy.
Conclusion
Understanding data encryption techniques isn’t optional anymore—it’s a digital life skill. We’ve covered the fundamentals: symmetric and asymmetric encryption, popular algorithms like AES and RSA, and practical tools you can start using today.
The key takeaway? Start small but start now. Enable device encryption, use encrypted messaging apps, and gradually build better security habits. Your future self will thank you when your data remains private and secure.
Take action today: Choose one encryption tool from this guide and implement it this week. Your digital security journey begins with a single encrypted step.
Frequently Asked Questions
How secure is AES-256 encryption against modern hacking attempts?
AES-256 is considered virtually unbreakable with current technology. Even the most powerful supercomputers would need billions of years to crack it through brute force. However, security depends on proper implementation and key management, not just the algorithm strength.
What’s the difference between SSL, TLS, and HTTPS encryption?
SSL (Secure Sockets Layer) is the predecessor to TLS (Transport Layer Security), which provides the encryption for HTTPS connections. When you see the lock icon in your browser, you’re using TLS encryption (often still called SSL colloquially) to protect data between your browser and the website.
Can I use both symmetric and asymmetric encryption together?
Absolutely! This hybrid approach is standard practice. Asymmetric encryption establishes a secure connection and exchanges symmetric keys, then symmetric encryption handles the actual data transfer. This combines the security benefits of asymmetric encryption with the speed of symmetric encryption.
Is open-source encryption software safer than proprietary solutions?
Open-source encryption often provides better security because the code is publicly auditable. Security experts worldwide can examine it for vulnerabilities. However, both open-source and reputable proprietary solutions can be secure when properly implemented and regularly updated.
How often should I rotate my encryption keys?
Key rotation frequency depends on your security requirements and the type of data being protected. For most personal use, annual rotation is sufficient. Businesses handling sensitive data might rotate keys quarterly or monthly. The important thing is having a consistent rotation schedule and secure backup procedures.
Sources: