Last Tuesday, a mid-sized accounting firm in Denver woke up to their worst nightmare—client tax returns scattered across the dark web. The culprit? A single employee who clicked on what looked like a routine invoice email. Sound familiar? If you’re breaking into a cold sweat right now, you’re not alone. Data breach prevention isn’t just an IT buzzword anymore; it’s the difference between staying in business and explaining to clients why their social security numbers are for sale online.
In this guide, we’ll walk through battle-tested cybersecurity strategies that actually work—no tech jargon overload, just practical steps you can implement starting today. Whether you’re running a three-person startup or managing a 500-employee operation, these data protection best practices will help you sleep better at night.
Why Data Breaches Are Every Business Owner’s Problem
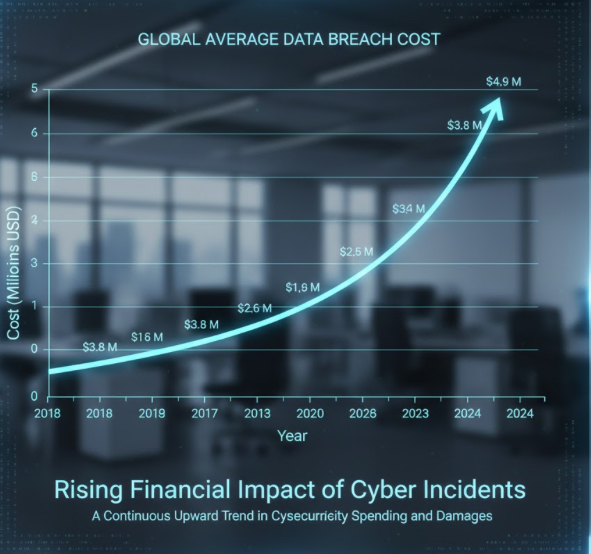
Here’s the uncomfortable truth: the average cost of a data breach hit $4.88 million in 2024, according to IBM’s Cost of a Data Breach Report. But beyond the financial hit, there’s the reputation damage, the legal headaches, and those sleepless nights wondering if you did enough.
Most business owners think, “We’re too small to be a target.” Wrong. Cybercriminals love small businesses—they’re like unlocked cars in a parking lot. You don’t need Fort Knox-level security, but you do need the basics done right.
The Foundation: Multi-Factor Authentication and Access Control
Let’s start with the low-hanging fruit that stops 99% of automated attacks: multi-factor authentication (MFA). Think of MFA as requiring both a key AND a fingerprint to open your safe. Even if someone steals your password, they’re stuck at the door.
Privileged Access Control: Not Everyone Needs the Keys to Everything
Here’s where most businesses mess up—giving every employee access to everything “just in case.” That summer intern doesn’t need access to your financial database. Your marketing team doesn’t need admin rights to your CRM.
Best practices for privileged access control:
- Grant minimum necessary permissions (the “least privilege” principle)
- Review access rights quarterly—people change roles, leave companies, or just don’t need that access anymore
- Use tools like Okta Identity Cloud or CyberArk Privileged Access Security to automate access management
- Separate admin accounts from daily-use accounts (yes, even for executives)
Encryption Techniques: Making Stolen Data Worthless
Imagine a thief breaks into your office and steals a filing cabinet. If everything inside is written in unbreakable code, did they really steal anything valuable? That’s encryption in a nutshell.
Encryption must-haves:
- Data at rest: Encrypt everything on your servers, laptops, and backups
- Data in transit: Use SSL/TLS certificates for websites and VPNs for remote access
- Email encryption: Because clicking “send” shouldn’t mean broadcasting secrets
Tools like Thales CipherTrust Data Security Platform and Trend Micro Data Security make enterprise-grade encryption accessible even for smaller teams. The best part? Once it’s set up, it works invisibly in the background.
Employee Training: Your Human Firewall
I’ve got news for you—your employees are either your strongest defense or your biggest vulnerability. There’s no in-between.
Security Awareness Training That Actually Sticks
Forget boring PowerPoints about password complexity. Real security awareness training involves:
- Simulated phishing attacks (yes, fake-attack your own employees monthly)
- Real-world scenarios: “What do you do if someone calls claiming to be from IT?”
- Gamification: Make security training competitive with leaderboards
- Quick monthly refreshers, not annual four-hour snoozefests
Insider threat mitigation starts with culture. Employees who feel valued and informed become your eyes and ears. Those who feel micromanaged and distrusted? They become risks.
The Tech Stack: Essential Tools for Data Protection
You don’t need twenty different security products. You need the right ones, properly configured. Here’s the practical stack:
| Security Layer | Purpose | Recommended Solutions |
|---|---|---|
| Endpoint Protection | Stops malware and ransomware | CrowdStrike Falcon, Microsoft Defender |
| Network Security | Monitors and blocks threats | Sophos XG Firewall, Palo Alto Networks Prisma Cloud |
| SIEM Platform | Detects anomalies in real-time | Splunk SIEM, IBM Security QRadar |
| Data Loss Prevention | Prevents sensitive data leaks | Symantec DLP, Varonis Data Security Platform |
| Backup & Recovery | Restores operations after incidents | Acronis Cyber Protect |
Incident Response Planning: Hope for the Best, Plan for the Worst
You know what’s worse than a data breach? A data breach where everyone panics because nobody knows what to do. An incident response plan is your playbook for crisis mode.
Your plan should answer:
- Who gets notified first? (Hint: Legal, IT, and executive leadership)
- How do we contain the breach within the first hour?
- What communication goes to customers, and when?
- Who’s talking to law enforcement and regulators?
Practice this plan twice a year minimum. Run tabletop exercises where you simulate breaches. It feels silly until it isn’t.
Third-Party Risk Management: Your Vendors Are Your Problem
Remember that Denver accounting firm? The breach actually started through their payroll software vendor. Welcome to the nightmare of third-party risk management.
Third-party vendor security assessment checklist:
- ✅ Do they have SOC 2 Type II certification?
- ✅ What’s their incident response history?
- ✅ Do they carry cyber insurance?
- ✅ Can they demonstrate regular security audits?
- ✅ What data do they actually need access to?
Platforms like Secureframe GRC Automation Platform automate vendor risk assessments so you’re not drowning in spreadsheets.
Cloud Data Breach Prevention: New Territory, Old Rules
Cloud security isn’t magic, and it’s definitely not “someone else’s problem” just because your data lives on AWS or Azure. Cloud data breach prevention strategies require:
- Proper IAM (Identity and Access Management) configuration
- Encryption of cloud-stored data
- Regular configuration audits (misconfigurations cause 80% of cloud breaches)
- Cloud Access Security Brokers (CASBs) for visibility
Palo Alto Networks Prisma Cloud and similar tools provide unified cloud security across multi-cloud environments.
The AI Advantage: Automation and Threat Detection
Here’s where things get interesting. AI tools for cybersecurity threat detection can spot patterns humans miss—like that employee who suddenly started downloading gigabytes of customer data at 2 AM.
Modern solutions like CrowdStrike Falcon use machine learning to identify zero-day threats before they’re officially “known.” It’s like having a security analyst who never sleeps, never takes vacations, and processes millions of events per second.
Software Updates: The Boring Thing That Actually Matters
I know, I know—nobody likes updating software. But here’s the thing: regular software updates patch the vulnerabilities criminals use to break in. WannaCry, one of the most destructive ransomware attacks ever, exploited a Windows vulnerability that Microsoft had patched months earlier. Companies that hadn’t updated? Toast.
Automate this wherever possible. Set critical security updates to auto-install during off-hours. Your IT team will thank you.
Password Management: Stop Writing Them on Sticky Notes
Let’s talk about passwords—specifically, how humans are terrible at creating and remembering them. “Spring2025!” isn’t clever; it’s the first thing hackers try.
Best password management tools for businesses:
- 1Password Business – User-friendly with great sharing features
- LastPass Enterprise – Integrates well with existing systems
- Bitwarden – Open-source and cost-effective
With a password manager, employees can have unique, complex passwords for every service without memorizing anything except one master password.
Compliance and Legal: The Framework Matters
Depending on your industry, you’re probably governed by regulations like GDPR, HIPAA, CCPA, or PCI-DSS. These aren’t just bureaucratic hoops—they’re actually solid cybersecurity frameworks for data protection.
Following frameworks like NIST Cybersecurity Framework or ISO 27001 gives you a roadmap. Plus, when (not if) you face an audit or breach investigation, having documented compliance helps immensely.
Real Talk: What Small Businesses Can Actually Afford
I get it—not every company has a million-dollar security budget. If you’re a small business, start here:
How to prevent data breaches in small businesses (essentials only):
- MFA on everything—email, banking, CRM, everything
- Cloud backup with encryption (starts around $10/month)
- Basic endpoint protection (many options under $5/user/month)
- Monthly security awareness emails
- A written incident response plan (free—just takes an afternoon)
You can build from there as you grow. Security isn’t all-or-nothing.
Warning Signs: How to Detect a Breach Early
Sometimes breaches simmer for months before exploding. Watch for:
- Unusual network traffic patterns
- Employees reporting strange system behavior
- Unexpected access attempts in logs
- Files encrypted or renamed mysteriously
- Customer complaints about suspicious communications
Detection tools like Rapid7 InsightIDR or Varonis can alert you to these red flags automatically.
Conclusion: Protection Is a Process, Not a Purchase
Here’s the bottom line: data breach prevention isn’t about buying one magical product or implementing one perfect strategy. It’s about layers—multiple defenses that work together, regular reviews and updates, and a culture where security is everyone’s job.
Start with the basics: MFA, encryption, employee training, and regular backups. Build from there based on your specific risks and budget. Most importantly, don’t wait until you’re that Denver accounting firm explaining to clients why their data is compromised.
Take action today: Pick one thing from this list and implement it this week. Next week, pick another. Progress beats perfection.
What’s your biggest security concern right now? Drop a comment below—I read every one and often feature reader questions in future posts.
Frequently Asked Questions
Q: How often should passwords be updated to prevent breaches?
A: Modern guidance has shifted—instead of forcing monthly changes (which leads to weak, predictable passwords), focus on strong, unique passwords for each service using a password manager. Change passwords immediately if there’s any suspected compromise or if a service you use reports a breach. The National Institute of Standards and Technology (NIST) now recommends length and uniqueness over frequent changes.
Q: Can encryption fully protect against data breaches?
A: Encryption is incredibly powerful but not a complete solution by itself. It protects data if stolen, but doesn’t prevent the initial breach. You also need access controls, monitoring, and employee training. Think of encryption as locking your valuables in a safe—essential, but you still need doors, alarms, and awareness of who’s in your building.
Q: What role does employee training play in data breach prevention?
A: Employee training is absolutely critical—human error causes up to 88% of data breaches, according to Stanford University research. Regular security awareness training transforms employees from your biggest vulnerability into your first line of defense. Monthly training sessions, simulated phishing tests, and clear reporting procedures dramatically reduce breach risk.
Q: How can small businesses protect sensitive data effectively?
A: Small businesses should focus on high-impact, low-cost measures: enable multi-factor authentication everywhere, use encrypted cloud backup services, implement basic endpoint protection, train employees on phishing recognition, and create a simple incident response plan. Many effective solutions like Microsoft Defender and Google Workspace security features are included with existing subscriptions.
Q: What are insider threats and how can they be mitigated?
A: Insider threats come from employees, contractors, or partners who misuse their authorized access—either maliciously or accidentally. Mitigation strategies include least-privilege access controls, monitoring unusual data access patterns, regular access reviews, creating a positive security culture, and using tools like Forcepoint Insider Threat or Varonis to detect anomalous behavior. Exit procedures are equally important—immediately revoke access when people leave.
Q: How soon should a data breach be reported?
A: Timing varies by regulation: GDPR requires notification within 72 hours of discovery, HIPAA requires 60 days for certain breaches, and most U.S. state laws have specific timeframes. Internally, you should activate your incident response plan immediately upon suspicion. For legal reporting requirements, consult with legal counsel familiar with your specific regulatory obligations, as penalties for late reporting can be severe.
Sources
- IBM Security – Cost of a Data Breach Report 2024: https://www.ibm.com/reports/data-breach
- National Institute of Standards and Technology (NIST) – Digital Identity Guidelines: https://pages.nist.gov/800-63-3/
- U.S. Federal Trade Commission – Data Breach Response Guide: https://www.ftc.gov/business-guidance/resources/data-breach-response-guide-business