Introduction
At 3 AM on a Tuesday, Jessica’s phone exploded with alerts. As the newly appointed security lead at a growing fintech startup, she watched in real-time as suspicious login attempts multiplied across their network. No playbook. No dedicated team. Just her, a laptop, and growing panic.
Sound familiar?
Building an effective Security Operations Center isn’t just about buying expensive tools or hiring a handful of analysts. It’s about creating a living, breathing defense mechanism that never sleeps, never blinks, and stands between your organization and the chaos of modern cyber threats.
Whether you’re starting from scratch like Jessica or upgrading an overwhelmed IT department doing security on the side, this guide will walk you through building a SOC that actually works—without burning through your budget or your sanity.
What Exactly Is a Security Operations Center?
Think of a SOC as your organization’s cybersecurity command center. It’s where trained analysts monitor networks 24/7, hunting threats, investigating incidents, and responding to attacks before they become disasters.
But here’s what separates a real SOC from just “the IT team doing security stuff”:
- Continuous monitoring: Not 9-to-5, but round-the-clock vigilance
- Dedicated personnel: Specialists focused solely on security, not multitasking with help desk tickets
- Integrated technology: SIEM platforms, SOAR automation, threat intelligence—all working together
- Defined processes: Incident response playbooks, escalation procedures, and documented workflows
A SOC isn’t a luxury anymore. With the average data breach costing $4.45 million in 2024, it’s become survival equipment.
The Core Components Every SOC Needs
People: Building Your Cyber Defense Dream Team
You can’t automate your way out of every security problem. SOC team roles typically include:
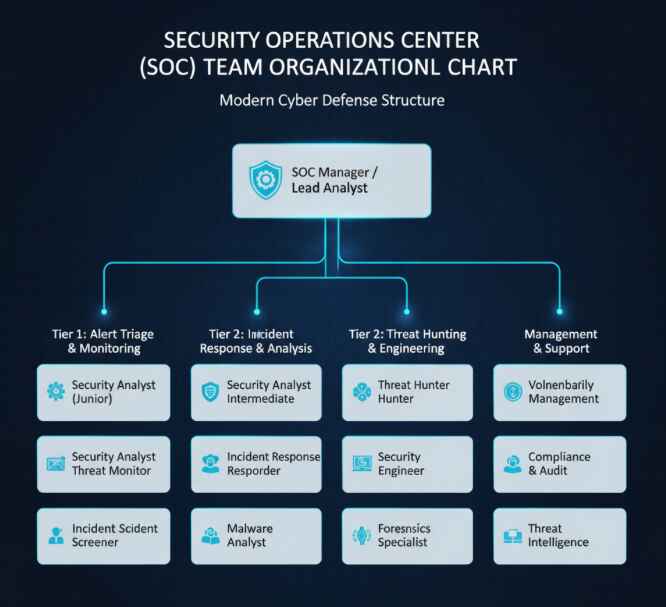
Tier 1 Analysts (The Frontline) These folks triage alerts, separating real threats from false positives. They’re monitoring dashboards, validating alerts, and escalating anything suspicious. Entry-level doesn’t mean unimportant—they’re your first line of defense.
Tier 2 Analysts (The Investigators) When Tier 1 escalates, these mid-level analysts dig deeper. They perform forensic analysis, correlate events across systems, and determine threat severity. Think of them as the detectives of your SOC.
Tier 3 Analysts/Threat Hunters (The Specialists) These senior experts proactively hunt threats that automated tools miss. They reverse-engineer malware, develop detection rules, and mentor junior analysts. Threat hunting techniquesthis advanced require deep technical expertise and creativity.
SOC Manager Orchestrates the entire operation, manages resources, reports to leadership, and ensures the team has what they need to succeed.
Technology: The Tools That Power Your SOC
Here’s where rubber meets road. Your technology stack needs to work seamlessly together:
| Technology Category | Purpose | Example Solutions |
|---|---|---|
| SIEM (Security Information and Event Management) | Centralized log collection and correlation | Splunk Enterprise Security, IBM QRadar, Microsoft Azure Sentinel |
| SOAR (Security Orchestration, Automation, and Response) | Automate repetitive tasks and workflows | Palo Alto Cortex XSOAR, Rapid7 InsightConnect |
| EDR (Endpoint Detection and Response) | Monitor and protect endpoints | SentinelOne Singularity, Cybereason Defense Platform |
| Threat Intelligence Platforms | Context about emerging threats | ThreatConnect, integrated feeds in SIEM |
| Network Detection and Response | Identify anomalies in network traffic | ExtraHop Reveal(x), Cisco SecureX |
Pro insight: Don’t buy everything at once. Start with a solid SIEM foundation, then layer in SOAR automation as your team matures. I’ve seen too many organizations drown in unused security tools they purchased but never properly implemented.
Processes: The Playbooks That Guide Action
Technology and talent mean nothing without clear processes. Your SOC needs documented procedures for:
- Incident classification: How do you categorize and prioritize threats?
- Escalation criteria: When does a Tier 1 alert become a Tier 3 emergency?
- Communication protocols: Who gets notified when, and through what channels?
- Evidence preservation: How do you maintain chain of custody for forensic analysis?
The best incident response playbooks read like choose-your-own-adventure books: “If you detect X, do Y. If result is Z, proceed to page 47.”
Step-by-Step: How to Build Your SOC from the Ground Up
Step 1: Define Your Requirements and Scope
Before buying a single tool or hiring anyone, answer these questions:
- What assets need protection most? (Customer data? Intellectual property? Financial systems?)
- What’s your threat landscape? (Industry-specific attacks you’re likely to face)
- What compliance requirements apply? (HIPAA, PCI-DSS, GDPR, etc.)
- What’s your realistic budget?
Be honest about your starting point. A 50-person startup needs a different SOC than a Fortune 500 enterprise.
Step 2: Choose Your Operating Model
You’ve got options here, and there’s no single right answer:
In-House SOC
- Pros: Complete control, custom-tailored to your environment
- Cons: Expensive, requires specialized hiring, 24/7 coverage is brutal
SOC as a Service (SOCaaS)
- Pros: Instant expertise, 24/7 coverage, predictable costs
- Cons: Less control, potential communication gaps, dependency on external provider
Hybrid Model
- Pros: Best of both worlds—internal team for customization, external support for coverage gaps
- Cons: Complexity in coordination
For most mid-sized organizations, SOCaaS or hybrid models make financial sense. You get enterprise-grade security without enterprise-grade overhead.
(Source: JumpCloud IT Index – What is a SOC)
Step 3: Implement Your SIEM Platform
Your SIEM is the heart of your SOC. It ingests logs from every corner of your environment, correlates events, and surfaces threats that would be invisible in isolation.
Best SIEM tools for SOCs in 2025 include:
- Splunk Enterprise Security: Industry leader with powerful analytics, but premium pricing
- Microsoft Azure Sentinel: Cloud-native with excellent Azure integration
- IBM QRadar: Strong AI-driven threat detection
- LogRhythm NextGen SIEM: Great balance of features and cost
Start by integrating your highest-value data sources: firewalls, authentication systems, critical servers. You can expand coverage over time.
Step 4: Layer in Automation with SOAR
Here’s a dirty secret: SOC analysts spend 60% of their time on repetitive tasks that machines should handle. Password resets, basic alert triage, gathering context data—this is where automating SOC workflows with SOAR transforms productivity.
Palo Alto’s Cortex XSOAR and similar platforms turn complex response procedures into automated playbooks. Receive a phishing alert? The SOAR platform automatically pulls email headers, checks URL reputation, queries threat intelligence feeds, and presents analysts with everything they need to make a decision—in seconds instead of minutes.
Step 5: Build Continuous Monitoring and Threat Hunting Capabilities
Continuous security monitoring means someone (or something) is always watching. But passive monitoring isn’t enough anymore.
Advanced persistent threats don’t trigger alarms—they blend in. That’s where proactive threat hunting comes in. Your senior analysts should dedicate time each week to hunting for indicators of compromise, anomalous behaviors, and subtle signs of intrusion that automated tools miss.
Effective threat hunters ask questions like:
- “What would an attacker do after gaining initial access to our network?”
- “Are there any unusual patterns in authentication logs?”
- “Which privileged accounts show abnormal activity?”
Step 6: Establish Metrics and Continuous Improvement
You can’t improve what you don’t measure. Track SOC metrics like:
- Mean Time to Detect (MTTD): How quickly do you spot threats?
- Mean Time to Respond (MTTR): How fast do you contain incidents?
- False Positive Rate: How much noise versus real threats?
- Alert Volume: Are you drowning in alerts or properly tuned?
- Threat Coverage: What percentage of MITRE ATT&CK techniques can you detect?
These numbers tell the story of your SOC’s effectiveness—and where you need to improve.
Common Challenges (And How to Overcome Them)
Alert Fatigue Is Real
One SOC I consulted for was drowning in 10,000 alerts daily. Analysts became numb to notifications, missing critical incidents buried in noise.
Solution: Aggressive tuning. Ruthlessly eliminate false positives. Use ML-powered tools to baseline normal behavior. Better to investigate 100 high-confidence alerts than ignore 10,000 meaningless ones.
The Talent Shortage Isn’t Going Away
Finding qualified SOC analysts is tough. Keeping them is tougher.
Solution: Invest in training programs for SOC analysts. Grow your own talent. Create clear career paths. Let junior analysts shadow senior threat hunters. Make your SOC the place where security professionals want to develop their skills.
Tool Sprawl Creates Blind Spots
Buying every shiny security tool creates integration nightmares. Gaps emerge where tools don’t communicate.
Solution: Platform consolidation. Choose tools that integrate natively. Palo Alto’s Cortex XDR combines endpoint, network, and cloud data in a single platform. Microsoft’s security ecosystem plays well together. Integration beats isolation every time.
The Future of Security Operations Centers
Cloud security is fundamentally changing SOC operations. Your perimeter isn’t a firewall anymore—it’s distributed across SaaS applications, IaaS infrastructure, and remote workers.
Modern SOCs need visibility into:
- Multi-cloud environments (AWS, Azure, GCP)
- SaaS application usage and data flows
- Container and serverless workloads
- IoT and operational technology
AI and machine learning will handle more of the routine work, letting human analysts focus on complex investigations and strategic threat hunting. The SOCs that thrive will blend human creativity with machine-scale analysis.
(Sources: BlueVoyant Knowledge Center – SOC | Elastic – What is a SOC)
Conclusion: Your SOC Journey Starts Now
Building an effective Security Operations Center isn’t a sprint—it’s a marathon with checkpoints. Start with clear requirements, choose the right operating model for your organization, implement foundational technologies, and continuously improve based on metrics and lessons learned.
Remember Jessica from the beginning? Six months after that 3 AM wake-up call, her organization now has a hybrid SOC with 24/7 monitoring, automated response playbooks, and a team that can handle incidents without panic.
Your organization deserves the same peace of mind.
Ready to take the next step? Share this guide with your security team, or drop a comment about your biggest SOC challenge. And if you’re evaluating SIEM platforms, check out our [comprehensive SIEM comparison guide] for detailed feature breakdowns.
Frequently Asked Questions
Q: What’s the difference between a SOC and a Network Operations Center (NOC)?
A: While both monitor systems 24/7, they have different focuses. A NOC ensures network availability and performance—think uptime, bandwidth, and connectivity. A SOC focuses exclusively on security threats, intrusions, and incident response. Many organizations confuse the two, but security operations require specialized skills and tools that go far beyond network management.
Q: How do I decide between building an in-house SOC versus using SOC as a service?
A: Consider three factors: budget, scale, and expertise. If you’re a small to mid-sized organization without existing security specialists, SOCaaS makes financial sense—you get enterprise-grade protection at a fraction of in-house costs. Large enterprises with complex, highly customized environments often benefit from in-house control. Many successful organizations use a hybrid approach: internal team for deep organizational knowledge, external SOCaaS for 24/7 coverage and specialized expertise.
Q: What’s the typical size of a SOC team?
A: It varies wildly by organization size and coverage needs. A minimal SOC might have 6-8 analysts (enough for basic 24/7 coverage with two per shift), plus a manager. Mid-sized organizations often run 15-20 personnel across all tiers. Enterprise SOCs can have 50+ people. More important than headcount is coverage: Can you respond to incidents at 3 AM on Sunday? Can your analysts take vacation without creating security gaps?
Q: How much does it cost to build and run a SOC?
A: Budget for $500K-$1M+ annually for a basic in-house SOC (salaries, tools, infrastructure). SOCaaS typically costs $5,000-$20,000 monthly depending on coverage level and organization size. Remember that costs include not just technology and salaries, but training, facility space (if physical SOC), and continuous tool optimization. Don’t forget opportunity costs—what security incidents would cost versus prevention.
Q: Can automation replace human SOC analysts?
A: Not entirely, though it dramatically amplifies their effectiveness. SOAR platforms can automate repetitive tasks like data gathering, basic alert triage, and routine response actions—freeing analysts for complex investigation and threat hunting. The future SOC blends human creativity, intuition, and contextual understanding with machine-speed analysis and pattern recognition. Think of automation as the analyst’s superpower, not their replacement.
Q: What qualifications should I look for when hiring SOC analysts?
A: For Tier 1 positions, look for Security+ or similar certifications, basic networking knowledge, and strong analytical skills. Tier 2 analysts benefit from CEH, GCIH, or similar credentials plus 2-3 years experience. Tier 3 threat hunters should have GCIA, GCFA, or OSCP certifications with deep technical expertise. But don’t overlook attitude and aptitude—curious, detail-oriented learners with strong communication skills often outperform credentialed candidates who lack passion. Many excellent analysts started in IT help desk roles and transitioned into security.