Last month, I watched a startup founder’s face turn pale as their security consultant delivered devastating news: a critical vulnerability in their app’s core architecture would require rebuilding 60% of their codebase. The fix? Six months and $2 million they didn’t have. “If only we had thought about security from the beginning,” he muttered.
This scenario plays out multiple times across different tech industry. But here’s the kicker—it’s completely preventable through implementing Security by Design principles. Instead of treating security as an afterthought, these principles weave protection into every fiber of your system’s DNA from day one.
In this guide, you’ll discover exactly how to embed security into your development process, why it saves massive headaches (and budgets) down the road, and the practical tools that make it happen seamlessly.
What Does Security by Design Actually Mean?
Security by Design isn’t just another buzzword—it’s a fundamental shift in how we approach system development. Think of it like building a house: you wouldn’t construct the entire foundation, walls, and roof before considering where the doors and windows go, right?
The same logic applies to software and systems. Security by Design means baking protection mechanisms into your architecture, code, and processes from the very first line of code you write.
The Seven Pillars of Security by Design
These core principles form the backbone of any secure system:
- Least Privilege Principle – Users get only the minimum access needed
- Defense in Depth – Multiple security layers protect against failures
- Fail Securely – Systems default to secure states when things go wrong
- Secure Defaults – Out-of-the-box configurations prioritize security
- Complete Mediation – Every access request gets verified
- Open Design – Security doesn’t rely on obscurity
- Psychological Acceptability – Security measures feel natural to users
Why Traditional “Security Later” Approaches Fail
I’ve seen too many development teams fall into the “we’ll add security later” trap. A CTO at a fintech company once told me, “We thought we’d just patch security holes as we found them. Turns out, that’s like trying to fix a leaky boat while it’s sinking.”
Here’s the brutal reality: fixing security issues after development costs 30 times more than building them in from the start. Plus, retrofitting security often breaks existing functionality, creating a nightmare scenario for both developers and users.
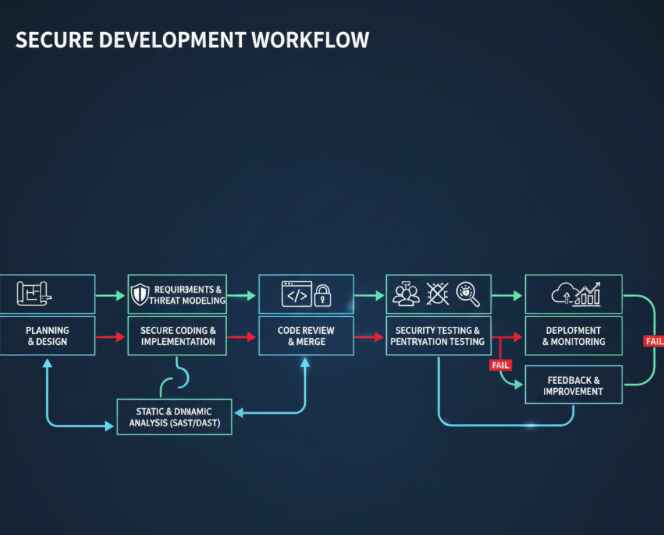
Integrating Security by Design in SDLC: A Practical Roadmap
Phase 1: Planning and Requirements
Start with threat modeling during your planning phase. Ask yourself:
- What could attackers target in our system?
- What’s the worst-case scenario if each component fails?
- How do we minimize attack surface area?
Tools like Microsoft Threat Modeling Tool make this process straightforward, even for teams new to security thinking.
Phase 2: Design and Architecture
This is where secure defaults and role-based access control become crucial. Design your system so that:
- Default configurations are the most secure options
- Users can’t accidentally expose sensitive data
- Access controls are granular and enforceable
Phase 3: Development
Secure coding practices take center stage here. Implement:
- Input validation at every entry point
- Proper error handling that doesn’t leak information
Essential Tools for Security by Design Implementation
Let me share the tools that actually work in real-world scenarios:
| Category | Tool | Best For | Integration Ease |
|---|---|---|---|
| Static Analysis | Veracode | Enterprise security scanning | High |
| Code Quality | SonarQube | DevOps pipeline integration | Very High |
| Threat Modeling | Microsoft Threat Modeling Tool | Early design phase | Medium |
| Dynamic Testing | OWASP ZAP | Web application security | High |
| Training | Secure Code Warrior | Developer education | Medium |
Static vs Dynamic Security Testing
Static Application Security Testing (SAST) catches vulnerabilities in your source code before deployment. Think of it as a spell-checker for security flaws. Tools like Checkmarx and Fortify excel here.
Dynamic Application Security Testing (DAST) tests your running application, simulating real-world attacks. Burp Suite Professional and Netsparker are go-to choices for many teams.
Balancing Usability and Security in System Design
Here’s where many teams struggle. You’ve probably heard the saying “security is the enemy of convenience”—but that’s outdated thinking. Modern Security by Design creates systems that are both secure AND user-friendly.
Take multi-factor authentication as an example. Traditional implementations made users jump through multiple hoops. Today’s solutions use biometrics, push notifications, and risk-based authentication that adapts to user behavior.
A UX designer I know puts it perfectly: “Good security design is invisible to legitimate users but impenetrable to attackers.”
DevOps and Security by Design: A Perfect Match
Security by Design in DevOps isn’t about slowing down your CI/CD pipeline—it’s about making security checks as automated as your deployment process.
GitLab Ultimate and similar platforms let you run security scans alongside your regular tests. When a vulnerability is detected, the build fails automatically. No human oversight needed for basic issues.
One development team I advised reduced their security review time from 2 weeks to 2 hours by automating their security testing pipeline.
Common Implementation Challenges (And How to Solve Them)
Challenge 1: Developer Resistance
Solution: Make security tools part of their existing workflow. Don’t ask developers to learn entirely new processes—integrate security into tools they already use.
Challenge 2: Performance Concerns
Solution: Implement security measures incrementally. Start with the most critical components and expand gradually.
Challenge 3: Budget Constraints
Solution: Begin with open-source tools like OWASP ZAP and SonarQube Community Edition. Prove ROI before investing in enterprise solutions.
Measuring Your Security by Design Success
Track these metrics to prove your implementation is working:
- Vulnerability discovery rate – Finding issues earlier in the development cycle
- Time to remediation – How quickly security issues get fixed
- Security debt accumulation – Preventing the buildup of unfixed vulnerabilities
- Developer security knowledge – Measured through training completion and secure coding assessments
The Future of Security by Design
AI-powered security tools are revolutionizing how we implement these principles. Machine learning algorithms can now predict potential vulnerabilities based on code patterns, while automated threat modeling adapts to new attack vectors in real-time.
Cloud-native security is also becoming essential. As more organizations move to containerized deployments, Security by Design principles must extend to orchestration platforms like Kubernetes.
Implementing Security by Design principles transforms how your organization approaches cybersecurity. Instead of playing defense against threats, you’re building systems that are inherently resistant to attacks.
The best part? You don’t need to revolutionize your entire development process overnight. Start small, pick one principle, implement it well, and expand from there. Your future self (and your security budget) will thank you.
Ready to make security a core part of your development DNA? Start by conducting a threat model for your next project, and share your experience in the comments below. What Security by Design principle will you implement first?
Frequently Asked Questions
What are the core principles of Security by Design?
The core principles include least privilege (giving users minimal necessary access), defense in depth (multiple security layers), failing securely (defaulting to safe states when errors occur), secure defaults (safe out-of-box configurations), complete mediation (verifying every access request), open design (not relying on security through obscurity), and psychological acceptability (making security feel natural to users).
How do you integrate Security by Design into software development?
Integration happens throughout the Software Development Life Cycle (SDLC): threat modeling during planning, secure architecture design, secure coding practices during development, automated security testing in CI/CD pipelines, and continuous monitoring post-deployment. Tools like GitLab Ultimate and Veracode help automate security checks within existing development workflows.
What is the principle of least privilege in Security by Design?
The least privilege principle means granting users, applications, and systems only the minimum access rights necessary to perform their intended functions. This reduces attack surface area and limits potential damage if an account is compromised. For example, a customer service representative shouldn’t have database administrator privileges—they only need access to customer records relevant to their role.
How does threat modeling support Security by Design?
Threat modeling systematically identifies potential security threats during the design phase, before code is written. It helps developers understand what attackers might target, how systems could fail, and which security controls are most critical. Tools like Microsoft Threat Modeling Tool guide teams through this process, making it easier to build security considerations into system architecture from the beginning.
What tools assist in implementing Security by Design principles?
Key tools include static analysis platforms (Veracode, Checkmarx), code quality analyzers (SonarQube), threat modeling software (Microsoft Threat Modeling Tool), dynamic testing tools (OWASP ZAP, Burp Suite), and comprehensive DevSecOps platforms (GitLab Ultimate). These tools integrate into development workflows to automate security checks and catch vulnerabilities early.
How to balance usability and security in design?
Modern Security by Design focuses on creating “invisible” security that protects without hindering legitimate users. This includes implementing risk-based authentication (stronger security measures only when needed), using biometrics and push notifications for seamless multi-factor authentication, providing clear error messages that guide users without revealing sensitive information, and designing intuitive interfaces for security features.
Sources:
- CISA Secure by Design – Official US government guidance on secure design principles
- UK National Cyber Security Centre – Cyber Security Design Principles – Comprehensive framework for implementing security by design
- Future Processing – Security by Design Guide – Practical implementation strategies for development teams