Introduction
At 2:47 AM on a Tuesday, Sarah’s phone exploded with alerts. As the IT director for a mid-sized financial firm, she’d seen her share of emergencies, but this was different. A ransomware attack had crippled their primary data center, and worse yet—their backup systems were compromised too.
While her team scrambled to assess the damage, one thought haunted her: “We have a business continuity plan, but did we really think through the information security aspects of business continuity?”
Sarah’s nightmare scenario plays out thousands of times each year across American businesses. According to recent studies, 60% of companies that suffer a major data breach go out of business within six months—not because they couldn’t recover their systems, but because they failed to protect their most valuable asset during the recovery process: their data.
In this comprehensive guide, we’ll explore how to weave bulletproof security into your business continuity strategy, ensuring that when disaster strikes, your sensitive information remains as protected as Fort Knox.
The Critical Connection: Why Security and Continuity Are Inseparable
Most businesses treat business continuity security controls as an afterthought—like remembering to lock your car after you’ve already walked away. But here’s the reality: disasters don’t pause cybersecurity threats; they amplify them.
During Hurricane Sandy in 2012, cyberattacks on affected businesses increased by 300%. Criminals know that during chaos, security protocols often get thrown out the window in favor of “getting back online quickly.” This is precisely when your data protection business continuity strategy becomes your lifeline.
Understanding the Security-Continuity Paradox
The challenge lies in balancing speed with security. You need to restore operations quickly, but not at the expense of exposing sensitive customer data, financial records, or intellectual property. It’s like performing surgery while running—technically possible, but requiring extraordinary skill and preparation.
Core Components of Secure Business Continuity
1. Encrypted Data Protection Throughout the Recovery Process
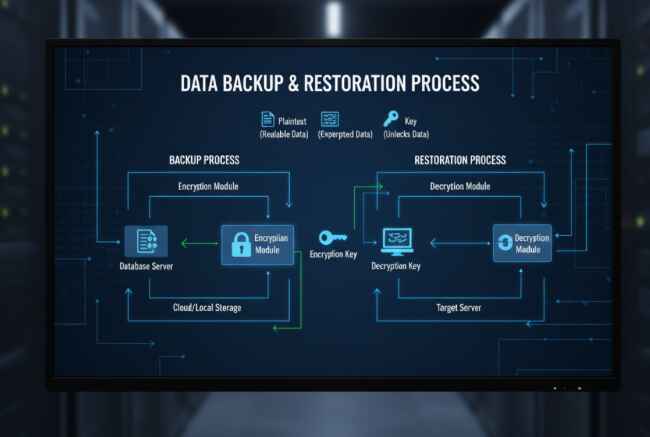
Your secure backup and recovery strategy should treat encrypted data like a precious family heirloom—never leaving it unprotected, even for a moment. Here’s what this looks like in practice:
- End-to-end encryption: Data remains encrypted during backup, transmission, and restoration
- Key management protocols: Secure storage and rotation of encryption keys, even during emergencies
- Zero-trust verification: Every data access request is verified, regardless of the emergency context
I once worked with a healthcare provider that discovered their “secure” backups were stored in plain text. During a system failure, they realized they couldn’t restore patient records without violating HIPAA compliance. The lesson? Test your encrypted backups before you need them.
2. Access Control Strategies for Crisis Situations
Continuity access control becomes exponentially more complex during emergencies. Your normal authentication systems might be offline, but you can’t just hand out master keys to everyone.
| Access Level | Normal Operations | During Crisis | Security Measures |
|---|---|---|---|
| Executive | Standard MFA | Emergency tokens | Biometric backup |
| IT Admin | Role-based access | Elevated privileges | Audit logging |
| General Staff | Limited permissions | Remote access VPN | Time-limited tokens |
| Contractors | Restricted access | Suspended until verification | Manual approval |
The key is preparing access control strategies for business continuity that maintain security while enabling rapid response. Think of it as having emergency keys that still require proper identification.
3. Cloud Security Business Continuity Integration
Cloud security business continuity offers unprecedented flexibility, but it also introduces new vulnerabilities. Your cloud recovery environment must be as secure as—if not more secure than—your primary infrastructure.
Consider implementing:
- Multi-region data replication with consistent security policies
- Cloud access security brokers (CASB) for enhanced visibility
- Identity and access management (IAM) that works across hybrid environments
4. Third-Party Risk Management During Disruptions
When systems fail, businesses often rush to engage emergency vendors and service providers. But third-party risk management in continuity planning can’t be ignored just because you’re in crisis mode.
Establish pre-approved vendor relationships with verified security credentials. It’s like having a list of trusted contractors ready before your roof starts leaking—you don’t want to vet them while water is pouring into your living room.
Advanced Security Considerations for Modern Business Continuity
Incident Response Business Continuity Integration
Your incident response business continuity protocols should flow seamlessly together. A security incident during a business continuity event creates a perfect storm that can destroy even well-prepared organizations.
Develop integrated playbooks that address scenarios like:
- Ransomware attacks during natural disasters
- Data breaches discovered during system recovery
- Insider threats exploiting crisis conditions
Remote Work Information Security During Disruptions
The COVID-19 pandemic taught us that remote work information security during disruptions isn’t optional—it’s essential. Your workforce might suddenly be distributed across dozens of home offices, coffee shops, and temporary locations.
Implement:
- Zero-trust network architecture that doesn’t rely on location
- Endpoint detection and response (EDR) for all remote devices
- Secure communication channels for crisis coordination
Compliance and Documentation Requirements
Business continuity compliance documentation becomes critical when regulatory bodies start asking questions after an incident. You need to prove that you maintained security standards even during the chaos.
Key documentation includes:
- Security control testing results
- Access logs during emergency operations
- Data handling procedures during recovery
- Vendor security assessments and approvals
Measuring Success: Metrics That Matter
Metrics for measuring security in business continuity help you understand whether your plans work before you desperately need them. Track:
- Recovery Time Objective (RTO) without compromising security
- Recovery Point Objective (RPO) with encryption validation
- Mean Time to Detect (MTTD) security issues during recovery
- Compliance audit scores during continuity exercises
Real-World Implementation: Learning from the Trenches
Last year, I consulted with a manufacturing company that experienced a perfect storm: a cyberattack during a power outage caused by severe weather. Their traditional business continuity plan fell apart because it didn’t account for the information security risks during business interruptions.
However, their competitor down the street had implemented integrated security-continuity protocols. While the first company took six weeks to fully recover (and lost three major clients), the second was back online in 48 hours with zero data compromise.
The difference? The successful company had spent two years embedding security into every aspect of their continuity planning, not treating it as a separate concern.
Conclusion
The information security aspects of business continuity aren’t just technical requirements—they’re business survival strategies. In our hyper-connected, data-driven economy, a business continuity plan without robust security integration is like a life raft with holes in the bottom.
Your organization’s ability to maintain data confidentiality, integrity, and availability during crises will determine not just whether you survive the storm, but whether you emerge stronger on the other side. The businesses that thrive in the next decade will be those that understand this fundamental truth: security isn’t what you add to business continuity—it’s what makes business continuity possible.
Ready to bulletproof your business continuity strategy? Start by auditing your current plans for security gaps, then gradually integrate the approaches we’ve discussed. Share this article with your leadership team, and consider scheduling a tabletop exercise that tests both your continuity and security responses simultaneously. Your future self—and your customers—will thank you.
Frequently Asked Questions
What role does information security play in business continuity planning?
Information security serves as the foundation of effective business continuity planning by ensuring data confidentiality, integrity, and availability during disruptions. It prevents security vulnerabilities from turning temporary operational interruptions into permanent business disasters through data breaches or compliance violations.
How can businesses maintain data protection during disaster recovery?
Businesses should implement end-to-end encryption for all backup and recovery processes, establish secure communication channels for crisis coordination, maintain strict access controls even during emergencies, and ensure all recovery procedures comply with regulatory requirements while being regularly tested and updated.
What are the key challenges in securing cloud-based business continuity solutions?
The main challenges include managing identity and access across hybrid environments, ensuring consistent security policies across multiple cloud regions, maintaining visibility into cloud security configurations, integrating cloud access security brokers, and balancing rapid scalability needs with security requirements during crisis situations.
How should organizations handle third-party vendor security during continuity events?
Organizations should pre-approve emergency vendors through security assessments, establish contractual security requirements for crisis situations, implement vendor access monitoring and logging, maintain emergency contact protocols with verified security credentials, and regularly review and update vendor security agreements.
What metrics should be used to measure information security effectiveness in business continuity?
Key metrics include Recovery Time Objective (RTO) without security compromises, Recovery Point Objective (RPO) with encryption validation, Mean Time to Detect security issues during recovery, compliance audit scores during continuity exercises, and the percentage of security controls that remain operational during various disruption scenarios.
How does zero trust architecture enhance business continuity security?
Zero trust architecture enhances business continuity security by removing location-based trust assumptions, continuously verifying every access request regardless of emergency status, providing consistent security policies across distributed recovery environments, enabling secure remote work during disruptions, and maintaining detailed access logs for compliance and forensics.
Sources: