Last month, a mid-sized financial firm I consulted for discovered something terrifying during their annual security review: attackers had been sitting in their network for over six months, quietly siphoning customer data. The breach wasn’t caused by sophisticated malware or zero-day exploits—it was a simple misconfigured server that nobody had noticed.
This wake-up call perfectly illustrates why comprehensive information security assessments aren’t just compliance checkboxes—they’re your digital lifeline. In today’s threat landscape, where cyberattacks cost businesses an average of $4.88 million per incident, a thorough security assessment can mean the difference between staying in business and becoming another cautionary tale.
Whether you’re a CISO looking to strengthen your security posture or a business owner trying to understand what these assessments actually involve, this guide will walk you through everything you need to know about conducting effective security assessments that actually protect your organization.
What Are Comprehensive Information Security Assessments?
Information security assessments are systematic evaluations of your organization’s security controls, policies, and infrastructure designed to identify vulnerabilities before attackers do. Think of them as a comprehensive health check-up for your digital assets—except instead of checking your blood pressure, we’re examining your firewall configurations, access controls, and data protection mechanisms.
A truly comprehensive assessment goes far beyond basic vulnerability assessment scans. It combines multiple evaluation techniques including risk assessment, penetration testing, compliance reviews, and threat prioritization to create a complete picture of your security landscape.
The goal isn’t just to find problems—it’s to understand your risk exposure, prioritize remediation efforts, and build a roadmap for continuous security improvement.
Core Components of Effective Security Risk Assessment
Asset Identification and Inventory
Before you can protect something, you need to know it exists. The foundation of any security posture evaluation starts with comprehensive asset discovery. This includes:
- Physical assets: servers, workstations, mobile devices, IoT devices
- Digital assets: applications, databases, cloud resources, intellectual property
- Human assets: employee access levels, third-party contractors, service providers
- Process assets: business workflows, data flows, security procedures
During one assessment, we discovered over 40 “shadow IT” cloud services that employees had implemented without IT knowledge—each one representing a potential data leak waiting to happen.
Risk-Based Vulnerability Analysis
Modern risk-based information security assessments focus on understanding not just what vulnerabilities exist, but which ones pose the greatest business risk. This involves:
Threat Modeling: Understanding who might attack you and why Impact Analysis: Determining what would happen if specific assets were compromised
Likelihood Assessment: Evaluating how probable different attack scenarios are Risk Scoring: Combining impact and likelihood to prioritize remediation efforts
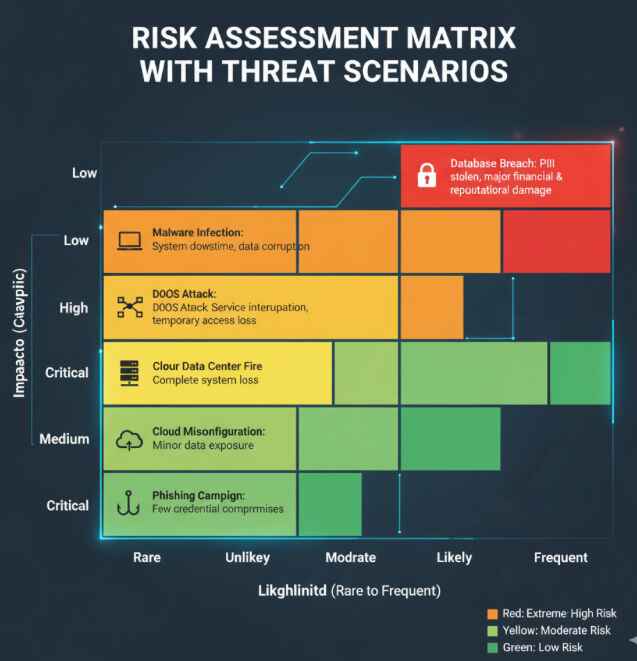
Technical Security Testing
The technical assessment phase combines multiple testing methodologies to uncover security gaps:
| Assessment Type | Purpose | Frequency | Tools Used |
|---|---|---|---|
| Automated Vulnerability Scanning | Identify known vulnerabilities | Weekly/Monthly | Tenable.io, Qualys, Nessus |
| Penetration Testing | Test exploitability of vulnerabilities | Quarterly/Annually | Burp Suite, Core Impact, Metasploit |
| Configuration Reviews | Validate security settings | Monthly | CIS Benchmarks, custom scripts |
| Access Control Audits | Review user permissions | Quarterly | Native tools, Tripwire Enterprise |
Essential Security Assessment Methodologies
Manual vs Automated Security Assessments
The age-old debate: should you rely on automated vulnerability scanning tools or invest in manual testing? The answer, like most things in security, isn’t black and white.
Automated assessments excel at:
- Continuous monitoring and baseline establishment
- Identifying known vulnerabilities at scale
- Compliance reporting and documentation
- Cost-effective regular scanning
Manual assessments shine when:
- Testing business logic flaws
- Conducting social engineering tests
- Exploring complex attack chains
- Validating automated findings
The most effective approach combines both methodologies. Use automated tools like Rapid7 InsightVM or Microsoft Defender Vulnerability Management for continuous monitoring, then supplement with manual testing to catch what machines miss.
Cloud Security Risk Assessment Practices
Cloud environments introduce unique assessment challenges that traditional tools weren’t designed for. AWS Inspector, Azure Security Center, and similar cloud-native tools help address these gaps by:
- Automatically discovering cloud resources across multiple accounts
- Checking for cloud-specific misconfigurations
- Monitoring for compliance with cloud security frameworks
- Integrating with DevOps pipelines for continuous assessment
One of our recent cloud assessments revealed that 60% of S3 buckets had overly permissive access policies—a finding that would have been impossible to detect with traditional network scanning tools.
Building Your Security Assessment Framework
Choosing the Right Assessment Tools
The security assessment tool market is crowded, but certain solutions consistently deliver exceptional value:
For Comprehensive Platform Coverage:
- Tenable.io: Excellent for large enterprise environments with mixed assets
- Qualys Cloud Platform: Strong compliance reporting and vulnerability management
- CrowdStrike Falcon Spotlight: Ideal for organizations already using CrowdStrike EDR
For Specialized Testing:
- Burp Suite Professional: Industry standard for web application testing
- Checkmarx: Leading SAST tool for secure code analysis
- OpenVAS: Cost-effective open-source option for smaller organizations
For Cloud-Specific Assessments:
- AWS Inspector: Native AWS security assessment
- Microsoft Defender: Integrated Microsoft environment scanning
- CyberArk Conjur: DevOps secrets and access security
Preparing for a Security Audit with Assessments
Security audit preparation often drives assessment timing, but this reactive approach misses the bigger picture. Instead of scrambling before audits, establish continuous assessment processes that keep you audit-ready year-round.
Key preparation steps include:
- Maintaining current asset inventories
- Documenting all security controls and their testing results
- Establishing clear remediation tracking and reporting
- Creating standardized assessment reports that map to compliance frameworks
Continuous Security Assessment Strategies
Traditional annual assessments are becoming obsolete. Modern threats evolve too quickly for once-a-year evaluation cycles. Continuous monitoring and assessment tools enable organizations to maintain real-time visibility into their security posture.
Effective continuous assessment programs typically include:
Daily: Automated vulnerability scanning of internet-facing assets Weekly: Full internal network scanning and asset discovery
Monthly: Configuration baseline validation and access reviews Quarterly: Comprehensive penetration testing and risk assessment updates Annually: Full-scope security program evaluation and strategic planning
Tools like F-Secure Radar and IBM Security Guardium excel at providing this continuous visibility while minimizing alert fatigue through intelligent risk scoring and prioritization.
Common Assessment Challenges and Solutions
Third-Party Security Risk Assessments
Modern organizations don’t operate in isolation. Third-party security risk assessments have become critical as supply chain attacks increase. However, assessing vendor security without access to their internal systems presents unique challenges.
Effective third-party assessment strategies include:
- Standardized security questionnaires based on industry frameworks
- On-site security reviews for critical vendors
- Continuous monitoring of vendor security posture through threat intelligence
- Contractual requirements for incident notification and security controls
Asset Discovery in Hybrid Environments
One of the biggest assessment challenges is achieving complete asset visibility across on-premises, cloud, and hybrid environments. Shadow IT, unauthorized devices, and sprawling cloud deployments create blind spots that attackers love to exploit.
Modern asset discovery requires:
- Network-based discovery using tools like Nmap and Lansweeper
- Agent-based inventory for detailed system information
- Cloud API integration for complete cloud resource visibility
- DNS analysis to identify forgotten subdomains and services
Measuring Assessment Effectiveness
How do you know if your assessment program is actually improving your security? Key metrics include:
Leading Indicators:
- Time to identify new vulnerabilities
- Percentage of assets with current security baselines
- Assessment coverage across all critical assets
Lagging Indicators:
- Mean time to remediate critical vulnerabilities
- Reduction in successful phishing attempts
- Improvement in compliance audit scores
The Future of Security Assessments
Security gap analysis techniques are evolving rapidly as threats become more sophisticated and environments more complex. Emerging trends include:
- AI-powered risk assessment for more accurate threat prioritization
- Integrated DevSecOps assessment tools that test security throughout the development lifecycle
- Behavioral analysis to identify insider threats and compromised accounts
- Quantum-safe cryptography assessment preparing for future threats
Conclusion
Comprehensive information security assessments aren’t just about checking boxes—they’re about building a culture of continuous security improvement that keeps pace with evolving threats. The organizations that thrive in today’s digital landscape are those that view assessments not as compliance burdens, but as strategic investments in business resilience.
Remember, the goal isn’t perfection; it’s progress. Start with the basics, establish regular assessment rhythms, and continuously refine your approach based on lessons learned and changing threats.
The question isn’t whether you can afford to invest in comprehensive security assessments—it’s whether you can afford not to. In a world where the average data breach costs nearly $5 million, even a modest assessment program pays for itself many times over.
Ready to strengthen your security posture? Start by evaluating your current assessment program against the frameworks we’ve discussed. What gaps do you see? Share your experiences in the comments below, or reach out if you need guidance developing a comprehensive assessment strategy for your organization.
Frequently Asked Questions
How often should organizations conduct comprehensive information security assessments?
The frequency depends on your risk profile and industry requirements, but most organizations benefit from quarterly technical assessments and annual comprehensive reviews. High-risk industries like finance and healthcare may need monthly assessments, while continuous automated scanning should run daily for all internet-facing assets.
What’s the difference between a vulnerability assessment and a penetration test?
A vulnerability assessment identifies and categorizes security weaknesses, while penetration testing attempts to exploit those vulnerabilities to demonstrate real-world impact. Think of vulnerability assessment as finding unlocked doors, while penetration testing involves actually walking through them to see what’s inside.
How long does a typical comprehensive information security assessment take?
Timeline varies significantly based on scope and organization size. A basic assessment for a small business might take 2-4 weeks, while comprehensive enterprise assessments can take 3-6 months. Factors affecting duration include number of systems, complexity of environment, and depth of testing required.
What should be included in a security assessment report?
Effective assessment reports should include executive summary with risk ratings, detailed vulnerability findings with remediation guidance, compliance gap analysis, risk prioritization matrix, and clear action plans with timelines. The report should be tailored to different audiences—technical details for IT teams, business impact summaries for executives.
How can small businesses conduct security assessments with limited budgets?
Start with free tools like OpenVAS for vulnerability scanning and NMAP for network discovery. Focus on the most critical assets first, and consider managed security service providers who offer assessment services at lower costs than hiring full-time security staff. Many cybersecurity frameworks like NIST provide free guidance for conducting basic assessments.
What role do compliance frameworks play in security assessments?
Compliance frameworks like PCI DSS, HIPAA, and SOX provide structured approaches to security assessments by defining specific controls to evaluate. However, compliance alone doesn’t guarantee security—effective assessments go beyond minimum compliance requirements to address organization-specific risks and emerging threats.
Sources:
- NIST Cybersecurity Framework: https://www.nist.gov/cyberframework
- CISA Cybersecurity Assessment Guide: https://www.cisa.gov/sites/default/files/2024-09/24_0828_safecom_guide_getting_started_cybersecurity_assessment_2022_final_508C.pdf
- SANS Security Assessment Resources: https://www.sans.org/security-resources/