Last month, I watched a seasoned CISO break into a cold sweat during a board meeting. The question was simple: “How does our security compare to industry standards?” His answer? A painful silence followed by “We don’t really measure that.” Don’t be that person. In today’s threat landscape, flying blind isn’t just risky – it’s career suicide.
Information security benchmarking and best practices aren’t just buzzwords thrown around in compliance meetings. They’re your GPS in the complex world of cybersecurity, helping you navigate from “we think we’re secure” to “we know exactly where we stand.” This guide will transform how you measure, compare, and improve your security posture, giving you the confidence to answer any board member’s question with data-driven precision.
Understanding Information Security Benchmarking: Beyond the Basics
Think of information security benchmarking as your security report card, but instead of comparing you to classmates, it measures your defenses against industry standards, peer organizations, and your own historical performance. It’s the difference between guessing and knowing.
I once worked with a healthcare organization that thought their firewall was bulletproof – until benchmarking revealed they were blocking only 60% of threats while industry peers averaged 95%. That wake-up call led to a complete security overhaul and, more importantly, prevented what could have been a catastrophic breach.
The Three Pillars of Security Benchmarking
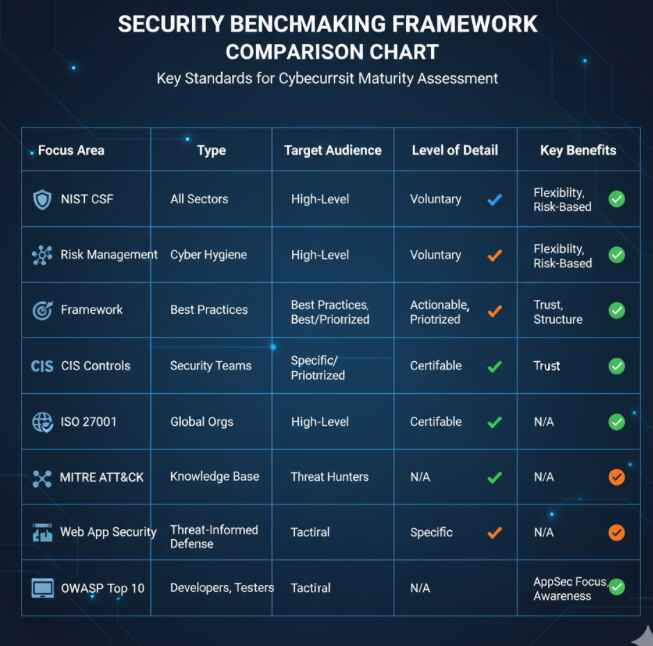
Standards-Based Benchmarking involves measuring against established frameworks like NIST, CIS Controls, or ISO 27001. These aren’t suggestions – they’re battle-tested roadmaps created from collective industry wisdom.
Peer Benchmarking compares your security metrics with similar organizations in your industry. It answers the crucial question: “Are we keeping up with the Joneses, or are we the weak link criminals target first?”
Internal Benchmarking tracks your progress over time, helping you understand whether your security investments are paying off or if you’re just spending money to feel better.
Essential Cybersecurity Best Practices: The Non-Negotiables
1. Risk Management in Cybersecurity: Know Your Enemies
Modern risk management in cybersecurity starts with understanding that threats evolve faster than your quarterly reviews. Effective organizations conduct continuous risk assessments, not annual checkbox exercises.
Here’s what separates the pros from the amateurs: they don’t just identify risks – they quantify them. Instead of saying “phishing is a problem,” they say “phishing attempts cost us an average of $50,000 per successful breach, occurring at a rate of 2.3 incidents per month.”
2. Security Performance Metrics That Actually Matter
Forget vanity metrics like “number of security tools deployed.” Focus on security performance metrics that predict real outcomes:
- Mean Time to Detection (MTTD): How quickly do you spot threats?
- Mean Time to Response (MTTR): How fast can you contain incidents?
- Security Control Coverage: What percentage of your attack surface is protected?
- Employee Security Awareness Score: How well can your people spot social engineering?
3. The NIST Cybersecurity Framework: Your North Star
The NIST cybersecurity framework isn’t just another acronym to memorize. It’s a practical blueprint that breaks security into five digestible functions: Identify, Protect, Detect, Respond, and Recover.
What makes NIST brilliant is its scalability. Whether you’re a three-person startup or a Fortune 500 corporation, the framework adapts to your needs without requiring a PhD in cybersecurity to understand.
Framework Showdown: Choosing Your Security Benchmarking Approach
| Framework | Best For | Key Strengths | Implementation Complexity |
|---|---|---|---|
| NIST CSF | Most organizations | Comprehensive, flexible | Medium |
| CIS Controls | Technical teams | Specific, actionable | High |
| ISO 27001 | Compliance-focused orgs | International standard | High |
| FAIR Risk Framework | Risk quantification | Financial metrics | Medium |
CIS Controls: The Tactical Playbook
CIS controls provide the “how” to NIST’s “what.” These 18 controls prioritize the most effective security measures, starting with basic inventory management (you can’t protect what you don’t know you have) and building up to advanced threat hunting capabilities.
Automated Security Benchmarking: Work Smarter, Not Harder
Manual benchmarking is like counting inventory by hand when you could use a barcode scanner. Automated security benchmarking solutions continuously assess your security posture, providing real-time insights instead of quarterly surprises.
Tools like CIS-CAT Pro Assessor can automatically evaluate your systems against hundreds of security benchmarks, while platforms like Tenable Nessus provide continuous vulnerability assessments that feed directly into your benchmarking dashboard.
The game-changer? These tools don’t just identify problems – they prioritize them based on actual risk to your business. No more playing whack-a-mole with endless vulnerability lists.
Peer Benchmarking in Cybersecurity: Learning from the Pack
Here’s where benchmarking gets interesting. Peer benchmarking in cybersecurity reveals whether you’re the gazelle or the lion in your industry ecosystem. I’ve seen organizations discover they were spending 300% more on security than peers while achieving 40% worse outcomes. That’s not dedication – that’s dysfunction.
Effective peer benchmarking considers factors like:
- Industry vertical (healthcare faces different threats than retail)
- Organization size (small businesses can’t implement enterprise solutions)
- Geographic location (GDPR vs. CCPA requirements)
- Technology stack (cloud-first vs. on-premises infrastructure)
Common Benchmarking Pitfalls: Learn from Others’ Mistakes
Mistake #1: Benchmark Theater Don’t measure things just because you can. Focus on metrics that drive decision-making and improve outcomes.
Mistake #2: One-Size-Fits-All Thinking Your security posture should reflect your unique risk profile, not copy someone else’s homework.
Mistake #3: Set-and-Forget Mentality Benchmarking isn’t a destination – it’s an ongoing journey. What worked last year might be obsolete today.
Building Your Security Benchmarking Program
Start small but think systematically. Choose one framework (I recommend NIST for beginners), identify 5-7 key metrics, and establish baseline measurements. Then gradually expand your program as your maturity grows.
Remember: perfect is the enemy of good. A simple benchmarking program that you actually use beats an elaborate system gathering dust.
The beauty of information security benchmarking and best practices lies not in achieving perfection, but in creating a culture of continuous improvement. Organizations that embrace benchmarking don’t just react to threats – they anticipate and prevent them.
Ready to transform your security posture from guesswork to precision? Start with one framework, choose three meaningful metrics, and begin measuring today. Your future self (and your board of directors) will thank you.
Share this guide with your security team and let us know in the comments: what’s the biggest benchmarking challenge your organization faces?
Frequently Asked Questions
What’s the difference between information security benchmarking and baselining?
Baselining establishes your current security posture as a starting point, while benchmarking compares your performance against external standards, peers, or best practices. Think of baselining as taking a photo of where you are today, and benchmarking as comparing that photo to where successful organizations should be. Both are essential: you need to know your current state before you can measure improvement against industry standards.
How often should organizations conduct security benchmarking?
The frequency depends on your risk profile and industry requirements, but most organizations benefit from quarterly formal benchmarking reviews with monthly metric tracking. High-risk industries like finance or healthcare often require monthly formal assessments. However, with automated security benchmarking solutions, continuous monitoring is becoming the gold standard, providing real-time insights rather than periodic snapshots.
Which security frameworks are best for small businesses starting their benchmarking journey?
Small businesses should start with the NIST Cybersecurity Framework because it’s scalable and doesn’t require extensive security expertise to implement. Focus initially on the “Identify” and “Protect” functions before advancing to more complex detection and response capabilities. The CIS Controls Top 6 (formerly Basic Controls) also provide an excellent tactical starting point for resource-constrained organizations.
What are the most important security metrics to track for effective benchmarking?
Focus on outcome-based metrics rather than activity metrics. Essential security performance metrics include: Mean Time to Detection (MTTD), Mean Time to Response (MTTR), percentage of critical vulnerabilities remediated within SLA, employee security awareness test scores, and security control coverage percentage. These metrics directly correlate with your ability to prevent, detect, and respond to security incidents.
How can organizations ensure their benchmarking efforts lead to actual security improvements?
Successful benchmarking requires three key elements: executive buy-in, actionable metrics, and regular review cycles. Don’t just measure – act on the insights. Establish clear improvement targets, assign ownership for each metric, and tie security performance to business objectives. Most importantly, celebrate progress and learn from setbacks rather than treating benchmarking as a compliance checkbox exercise.
Sources:
- National Institute of Standards and Technology (NIST) – Cybersecurity Framework: https://www.nist.gov/cyberframework
- Center for Internet Security (CIS) – CIS Controls and Benchmarks: https://www.cisecurity.org/cis-benchmarks
- Cybersecurity and Infrastructure Security Agency (CISA) – Cybersecurity Best Practices: https://www.cisa.gov/topics/cybersecurity-best-practices